Understanding VPN Protocols: 6 Protocols Compared in 2025
Quick Answer: Most Popular VPN Protocols Explained
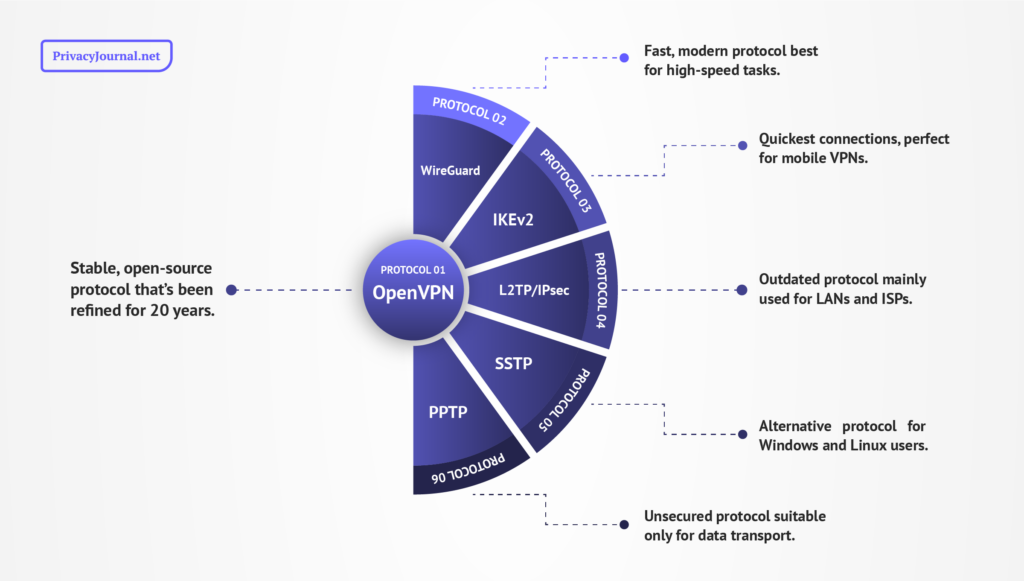
- OpenVPN — Stable, open-source protocol that’s been refined for 20 years
- WireGuard — Fast, modern protocol best for high-speed tasks
- IKEv2 — Quickest connections, perfect for mobile VPNs
- L2TP/IPsec — Outdated protocol mainly used for LANs and ISPs
- SSTP — Alternative protocol for Windows and Linux users
- PPTP — Unsecured protocol suitable only for data transport
VPN protocols lie at the heart of how a virtual private network keeps your internet connection safe and secure. Once you strip away all the ad blockers, bonus cloud storage and colorful graphics, the protocol is what remains, directly establishing the encrypted tunnel the VPN uses to get you online.
Despite their importance to establishing VPN protection, protocols are often misunderstood. VPN providers often boast about their protocol selection without explaining what terms like “OpenVPN” and “UDP” mean or when you should change your protocol — or even that protocols and VPN encryption are two completely different things.
Luckily, I’m here to help you out. In this post, I’ll define the six most common VPN protocols you’re likely to encounter while using any of the best VPN services. I’ll explain each protocol’s strengths and weaknesses, and then list the best options for use cases like streaming, torrenting and protecting your privacy. To start, let’s explore what a VPN protocol actually is.
What Are VPN Protocols?
A VPN protocol is a set of instructions that allows a VPN server to communicate with other devices on your behalf while maintaining encryption.
A protocol has two main functions:
- Encryption: Turning your data into nonsense so it can’t be read in transit.
- Authentication: Confirming each device’s identity in spite of the encryption.
Protocols aren’t just for VPNs — the entire internet runs on them. The hypertext transfer protocol (HTTP) shows us websites, whereas the internet protocol (the IP in “IP address”) gives devices a standard identity. Thanks to the transmission control protocol (TCP), any device can locate another one on the World Wide Web with just its IP address.
VPN protocols work the same way but with another layer of instructions. The new instructions allow the VPN server to act as a middleman between your device and the internet. The universal instructions let devices find each other even when most of the relevant data is encrypted. Not all VPN protocols include encryption — authentication is the truly indispensable element.
Comparison Table of VPN Protocols
| Protocol | Speed | Security | Encryption | Native OS |
|---|---|---|---|---|
| OpenVPN | Fast (TCP) Not very fast (UDP) | Uncrackable | Entire OpenSSL library* | N/A |
| WireGuard | Very fast | Uncrackable | ChaCha20 | N/A |
| IKEv2 | Very fast | Secure | Several types via IPsec | N/A |
| L2TP/IPsec | Fast | Secure | Several types via IPsec | N/A |
| SSTP | Very fast | Uncrackable | AES-256 | Windows |
| PPTP | Very fast | Not secure | MPPE | N/A |
The Most Common VPN Protocols
Let’s summarize what we’ve learned so far. A VPN protocol is a “language” that lets a VPN server relay instructions between your computer and the internet.
So, if there’s only one internet protocol, why are there so many VPN protocols? The main difference is the type of encryption each one uses, but this one difference has far-reaching implications.
OpenVPN
What OpenVPN is best for:
- Maintaining your security during normal online activity, especially if you want to set up a manual connection.
OpenVPN, a free VPN protocol that’s been around for almost 25 years, is the closest to a universal standard that exists in the VPN world. Open-source since launch, OpenVPN guarantees its security with something no other protocol has — an army of nerds who have been poking at its vulnerabilities since before the ‘Lord of the Rings’movies dropped.
Although OpenVPN is configured to use any encryption algorithm in the OpenSSL library, most VPN services set it to use the 256-bit advanced encryption standard, shortened to “AES-256.” This “military-grade” encryption takes more power to process than some alternatives, but the best VPNs can still wring fast internet out of it, as I explain in my NordVPN review.
Widely available and extensively vetted, OpenVPN is a common choice for people who prefer to set up their own encrypted connections without a VPN provider in the middle. Providers often use it to build their own protocols, such as VyprVPN’s Chameleon protocol, which I cover in my VyprVPN review.
UDP vs TCP
OpenVPN’s speed depends on how it transports data, which you can usually toggle in your VPN app.
- OpenVPN over TCP waits to confirm receipt of each data packet before it sends the next one, making it slower but more stable.
- OpenVPN over UDP (a user datagram protocol) doesn’t wait for confirmation, so your connection is faster but more likely to drop.
WireGuard
What WireGuard is best for:
- Streaming
- Torrenting
- Gaming
- Other activities that require maximized speed and stability
WireGuard is the “new kid” on the VPN block. Since its first release in 2016, it’s had the explicit goal of solving the problems with OpenVPN — chiefly, its occasional lags in speed and its large, unwieldy source code. Its main innovation is a symmetric key architecture based on Secure Shell (SSH) that authenticates devices faster than OpenVPN.
The downside is that this approach requires the VPN server to store your IP address in order to establish the connection. However, if you use a VPN with RAM-only servers, this is a non-issue — the server purges your IP address every time it resets, which occurs about once an hour. My Surfshark review explores how it makes WireGuard safe with this method.
By boosting speed without sacrificing security, WireGuard has quickly become the ideal secure VPN protocol for fast connections. It is a fixture of all the services on our best VPN for torrenting and best VPN for gaming lists. Like OpenVPN, WireGuard is open-source. Unlike OpenVPN, it works only over UDP.
IKEv2
What IKEv2 is the best for:
- Protecting mobile devices while you’re out and about.
Microsoft and Cisco jointly developed the VPN protocol “internet key exchange version 2” (IKEv2). It’s one of the three most common protocol options on modern VPNs, along with WireGuard and OpenVPN. On average, IKEv2 is the fastest of the three because it’s essentially two protocols hidden in a trenchcoat.
IKEv2 is more properly called IKEv2/IPsec, with IPsec standing for “internet protocol security.” IPsec is a VPN protocol on its own, but it requires a lot of manual configuration to connect two devices. When IKEv2 establishes the secure channel and then relies on IPsec protocol for the actual transport, together each does its job faster than either could alone.
This makes IKEv2 the ideal protocol for mobile devices. If your phone or tablet happens to move from one type of data network to another, IKEv2 will reconnect the fastest, minimizing downtime that could leave your internet connection unprotected. It’s a fixture of the entries on our best VPN for mobile list, though some avoid it because it’s not open source.
L2TP/IPsec
What L2TP/IPsec is best for:
- Transporting data on ISP networks or large-scale public WiFi
- Combining multiple local networks
Layer 2 tunneling protocol (L2TP) is a transportation protocol that lacks inherent security. It can send data between your device, a proxy and a web server, but none of it is encrypted on its own. Like IKEv2, L2TP is almost always paired with IPsec. Here, IPsec just handles encryption, not transport as with IKEv2.
L2TP/IPsec is an improvement on protocols like PPTP, which isn’t used much anymore. One problem is that the access port can easily be blocked, which means that firewalls frequently catch it — like those that enforce geoblocks on streaming services. If you’re looking for the best protocol to unblock Netflix, you’re better off sticking to the top half of this list.
OpenVPN, IKEv2 and WireGuard have almost wholly surpassed L2TP, and most VPNs no longer support it. However, it’s still useful for connecting certain types of networks. Businesses can use L2TP to connect private office networks in several locations, and internet service providers (ISPs) often use it to move customer data.
SSTP
What SSTP is best for:
- Backup in case OpenVPN is giving you trouble on Windows or Linux
Microsoft created the Secure Socket Tunneling Protocol (SSTP) as a Windows-native alternative to L2TP. It uses almost the exact same cryptography as OpenVPN — both authenticate connections using SSL/TLS, and both rely on AES-256 to encrypt the data itself. Due to this similarity, SSTP is most useful as an OpenVPN alternative.
The problem with SSTP is that it can’t measure up to OpenVPN where it counts. Whereas OpenVPN is open-source, SSTP works only natively on Windows. However, there are some workarounds to get it on macOS and Linux. Though OpenVPN can use both TCP and UDP for transport, SSTP only uses TCP, so you’re out of options if your TCP connection is too slow.
PPTP
What PPTP is best for:
- Remotely accessing networks, but you really shouldn’t use it at all.
Point-to-Point Tunneling Protocol (PPTP) is not a good VPN protocol. Its only built-in defense is Microsoft point-to-point encryption (MPPE), which relies on outdated keys that are easy to brute-force.
According to Edward Snowden, PPTP is so riddled with security flaws that the U.S. National Security Agency (NSA) can easily spy on connections that use it. Signal co-creator Moxie Marlinspike said back in 2012 that PPTP “should be considered unencrypted.”
Even if you don’t work for the NSA, cracking PPTP is so easy that teachers assign it as homework. PPTP wasn’t designed for security but rather for the original purpose of a VPN — to remotely access private computer networks. However, using it today might put that private network at risk. To be safe, use another protocol and ignore PPTP altogether.
Proprietary Protocols
What proprietary protocols are best for:
- It depends, but generally either normal browsing tasks or obfuscation.
Some VPN providers build their own protocols and keep them exclusive. Occasionally, they’re built from scratch — like NordVPN’s NordLynx, are reimplementations of OpenVPN or WireGuard.
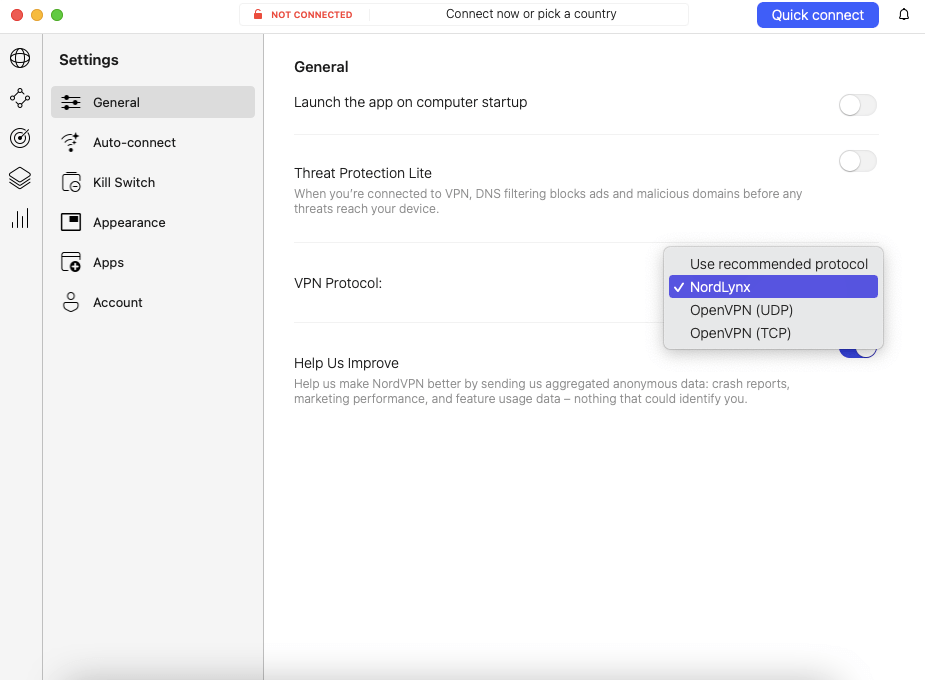
OpenVPN (UDP and TCP).
What’s the main use case for these unique protocols? To be honest, it’s advertising. Lightway and NordLynx are similar enough to WireGuard that their use cases are identical, except when it comes to selling ExpressVPN or NordVPN (both of which have plenty of better selling points).
I’m not saying that proprietary protocols don’t work. They do! They even occasionally bring something new to the table, like VyprVPN’s Chameleon, which has mastered fast obfuscation. I’m just saying that it rarely makes sense to consider them to be different from the protocols they’re based on.
Use Cases for Different VPN Protocols
As I’ve alluded to throughout the article, almost every VPN protocol has its place (except PPTP). There isn’t necessarily a “best VPN protocol” but rather better VPN protocols for certain use cases; so the most secure VPN protocol isn’t necessarily the fastest VPN protocol, and vice versa.
Most VPN providers offer multiple options for popular VPN protocols. For VPN users, having a wide selection is good — if one protocol were to become universal, any major flaws in that protocol could create a security catastrophe. Here are the best protocols for each major VPN use case.
Streaming
A streaming VPN needs two elements: servers that can get around copyright firewalls and fast-enough speeds to play videos once you’re in. Choose protocols with decent speeds that use the same ports as regular internet traffic. Our best Netflix VPN and best VPN for Hulu selections offer some or all of these.
Best protocols:
- OpenVPN over UDP
- WireGuard
- IKEv2
- SSTP
Downloads
For most downloads, speed is the most important factor. Since you aren’t trying to get around firewalls, unblocking ability takes a back seat. However, the fastest protocols also tend to be the best at unblocking, so this list is the same as the one above.
Best protocols:
- OpenVPN over UDP
- WireGuard
- IKEv2
- SSTP
Torrenting
ISPs frequently throttle your internet connection if they catch you using a torrenting client, even if you weren’t downloading illegal content. The most private protocols are the best in this case, so I’ve left out any that aren’t open-source (Microsoft owns IKEv2 and SSTP).
Best protocols:
- OpenVPN over UDP
- OpenVPN over TCP
- WireGuard
Privacy
If you’re mainly using a VPN to protect your identity and avoid hackers, you should pick the same protocols as the ones on the torrenting list above. These options are completely open, so analysts can confirm they don’t contain any known weaknesses.
Best protocols:
- OpenVPN over UDP
- OpenVPN over TCP
- WireGuard
Gaming
The most important factor for gaming is latency — you want a VPN connection with the shortest pings possible so data updates in real time. Use WireGuard on desktop and IKEv2 on mobile for the best experience.
Best protocols:
- WireGuard
- IKEv2
Conclusion: VPN Protocols Explained
The vast majority of the time you spend connected to a VPN, you won’t need to know anything about VPN protocols. The top providers include features to select the best protocol automatically. If you choose for yourself, you’ll almost always want to use OpenVPN, WireGuard or IKEv2.
That said, now that you know the differences between protocols, you’re ready to take even more control of your online security. You can make an active choice to trust the newer WireGuard or the less-open IKEv2. If you’d prefer to stick with OpenVPN, exchanging slower speeds for more trust, you can do so — and know to switch to UDP when TCP is too sluggish.
I hope you’ve become a more confident VPN user after reading this article. If you have any questions, I’d love to hear them in the comments. Do you prefer secure VPN protocols or the fastest VPN protocols for your use? Are there Other VPN protocols you think I should have included? Let me know. Thanks for reading!
FAQ: VPN Protocols
Which VPN Protocol Is Best for Streaming?
WireGuard and IKEv2 are almost always the best VPN protocols for streaming given their superior speeds. However, WireGuard is open-source, whereas Microsoft owns IKEv2’s source code.Is My VPN TCP or UDP?
Almost any VPN that supports OpenVPN will let you switch between TCP and UDP. TCP is more stable but occasionally suffers slowdowns. UDP is faster, though it may drop connections.Is WireGuard Better Than OpenVPN?
WireGuard is generally faster than OpenVPN and has a smaller codebase, which theoretically gives it fewer vulnerabilities to attack. However, OpenVPN has been tested and refined over a longer period of time. In reality, both are good for the same tasks.Which VPN Protocol Is the Fastest?
IKEv2 is most often the fastest protocol. With its power to create rapid-fire connections between devices, it’s perfect for mobile devices that move between networks.

Leave a Reply