
What Are the 4 Different Types of VPN Connection? Answered for 2025
Quick Answer: What Are the Four Main Types of VPN?
The four main types of VPN are VPN apps for individuals browsing the internet, remote access VPNs that connect devices with secured networks, site-to-site VPNs that share locked networks between locations, and extranets that control access to site-to-site networks.
Before virtual private networks (VPNs) were famous for protecting our data and putting a world of IP addresses at our fingertips — like my best VPN picks do — they were mostly known for remote access. Instead of a global server network, a VPN was a miniature internet for a closed institution or business. Those aren’t the only types of VPN connection, either.
You’ll hear various things from different experts, but to my mind, there are four principal types of VPNs: personal, remote access, site-to-site and extranet. All four are in common use today, though each one solves a different problem. Some are for individuals, some for organizations, and some even resemble their own miniature World Wide Webs.
In this article, I’ll go over the four main VPN types, along with any subcategories worth noting. I’ll explain the benefits of each and how to use them, with examples in each category. I also want to talk about VPN protocols, which differentiate how a network achieves VPN encryption. We’ve got a lot to cover, so let’s get started.
The 4 Types of VPN Connections Compared
Use the table below as a quick reference for the four main types of virtual private network.
| Type of VPN | How It Works | Who Is It For? | Use Cases | Examples |
|---|---|---|---|---|
| VPN App | User accesses a common server network through a VPN client interface | Individuals | Protect personal data; use public WiFi; change IP address | NordVPN, Surfshark, ExpressVPN, Proton VPN, CyberGhost |
| Remote Access VPN | User accesses a private server network | Individuals employed by organizations | Access proprietary company data while traveling or teleworking | GoodAccess, NordVPN Meshnet, Citrix Gateway |
| Site-to-Site VPN | Private networks in two or more locations are connected | Organizations with multiple sites | Give employees controlled access to data at other locations | NordLayer, Perimeter 81, Twingate |
| Extranet VPN | Private networks owned by two or more organizations are connected | Organizations that regularly work with outsized partners | Grant third parties controlled access to an organization’s intranet | Zscaler Private Access, Palo Alto Networks GlobalProtect, Cisco Dynamic Multipoint VPN |
This table is a necessary oversimplification. Although there are key differences between personal VPN apps and private business networks, the boundaries between remote access VPNs, site-to-site VPNs and extranets are quite blurred. Many of the providers I listed as examples for one type can actually provide all three services.
Furthermore, all four types share roughly the same use case: ensuring only authorized people can access sensitive information. For personal VPNs, the private data is in transit, while it’s at rest for the other three types — but they all have the same fundamental aim. They also use the same suite of VPN protocols to get the job done.
The key difference is scale. A VPN app user wants to access one point from another. A remote access VPN lets one point access a whole proprietary network. A site-to-site VPN lets one network converse with another, and an extranet VPN controls access to a network of site-to-site VPNs. It’s all about the number of users and the amount of nodes.
1. VPN Apps
- Can change your public IP address
- Can securely access the entire web
- Universally available
- Only accesses the provider’s servers
- Share IP addresses with strangers
- Good ones cost money
Who Is It For?
VPN apps are for individuals who want to get online securely for personal reasons. Unlike all the other types of VPNs, the purpose of a VPN app is to access the open internet, not the locked network of a business, school or other institution. In this case, “private network” refers to the selection of servers owned by the VPN provider.
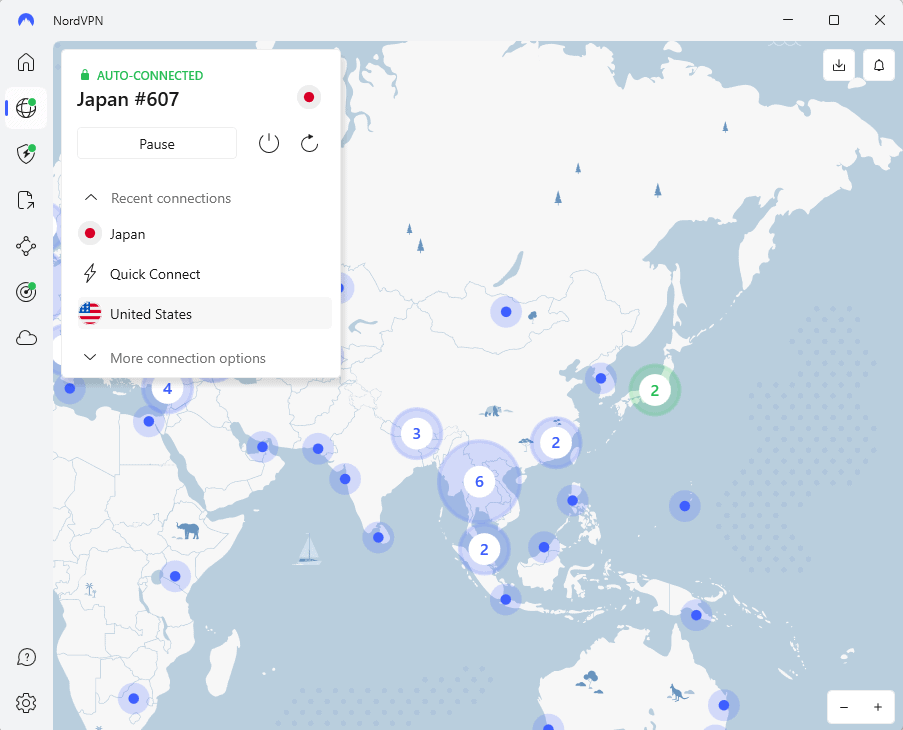
My article on the benefits of VPN protection explains in more detail why you’d want to do this, but basically, the VPN app is a menu of IP addresses you can use to mask your real identity. This protects your anonymity and privacy while also letting you access international content. Anyone with an internet connection can use a VPN app.
How It Works
You can get online safely with a VPN app by following these steps:
- Subscribe to a VPN service. Pick a well-reviewed provider and create an account on its website. Our list of the best cheap VPNs is a good starting point. Enter a payment method if necessary.
- Download the VPN app for your device. Almost all VPN providers support Windows, macOS, iOS and Android; many also have apps for Linux, web browsers and smart TVs. You can download apps from the VPN’s website or the appropriate mobile app store.
- Install the VPN app and log in. Open the downloaded file and your installation wizard will take you the rest of the way. Log in with the credentials you created in step one.
- Connect to a server location. This will be your proxy identity as you surf the net. Unless you need a specific location — say, if you’re trying to get Netflix unblocked in a certain country — pick a location near you for the best speeds.
- Get online as normal. Every request your browser sends will go through your chosen VPN server, so nobody can see what you’re actually doing.
Use Cases
VPN apps provide an encrypted connection through an alternate IP address. This is useful for several tasks:
- Foiling online surveillance: Internet service providers, intelligence agencies and advertisers are all known to spy on regular internet users. When you’re connected to a VPN app, they can’t trace your activity back to its source.
- Staying safe on public WiFi: Unsecured WiFi networks in cafes, hotel lobbies and other public places give hackers plenty of openings to exploit you with man-in-the-middle attacks. If you mask and encrypt your connection, criminals can’t isolate your device or hijack your communications.
- Streaming internationally: You can use a VPN to fool websites into thinking you’re in a different country and showing you that nation’s content. This lets you watch region-exclusive libraries, such as Canadian Netflix.
- Torrenting safely: Torrenting is legal as long as you don’t download any copyrighted files, but lots of ISPs throttle torrenting traffic with no regard for legality. With a VPN, your ISP can’t deduce whose internet traffic it’s supposed to be slowing down.
VPN App Examples:
- NordVPN — My personal VPN app choice, with fast infrastructure, a wide server network and well-defined features. Learn more in my NordVPN review.
- Surfshark — An affordable VPN with no limits on how many encrypted connections can share an account, which is perfect for families and small businesses. See my Surfshark review.
- ExpressVPN — A fast VPN that makes it easy to encrypt a direct connection between two devices. My ExpressVPN review has the story.
2. Remote Access VPN
- Can access closed networks from anywhere
- Maintains encryption on public WiFi
- Useful for remote troubleshooting
- Can’t access sites outside the dedicated network
- Cloud storage can replace most functions
- Vulnerable to weak passwords
Businesses, schools, government agencies and other organizations that are large enough to have offices frequently develop internal, password-protected networks. Devices on these networks can share files and messages freely, but nobody outside can see in, keeping trade secrets safe from the eyes of competitors.
That’s all well and good, but what about organizations where employees travel a lot? Or what if a pandemic forces the whole team to stay home? Your staff needs a way to get ahold of the private network when they can’t reach an on-site device. A remote access VPN is that solution, connecting any device to the on-site network from any location.
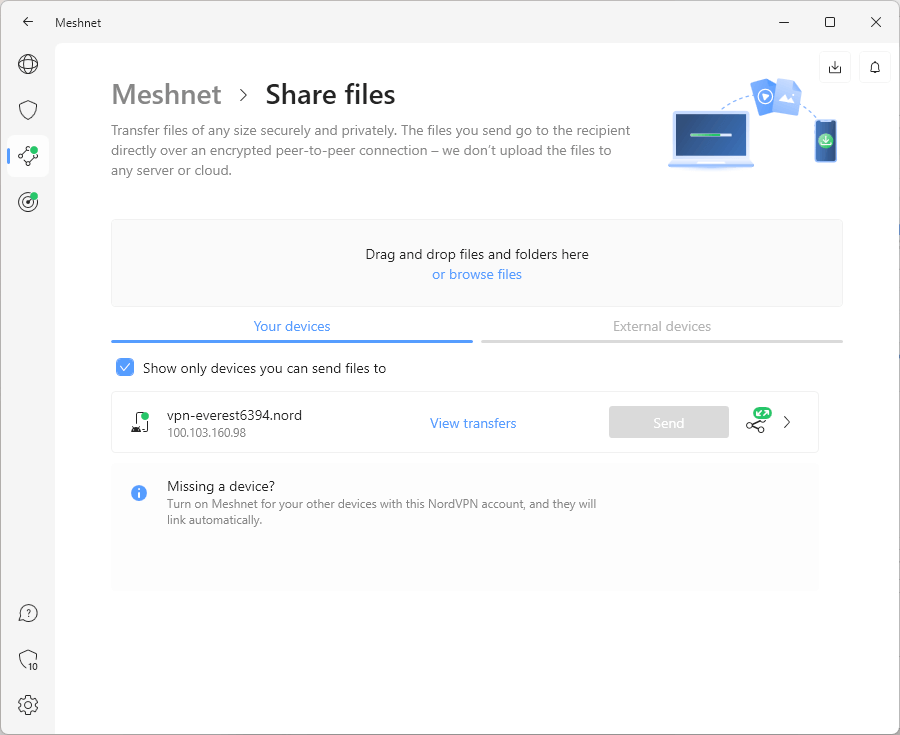
to one computer, you can access the whole network connected to that device.
Remote access VPNs use the same tunneling technology as VPN apps, just for an institutional intranet instead of the world wide web. Once connected, you can use a company computer like you were there in person. IT departments can even use VPNs to diagnose computer problems from afar, though you don’t need a VPN to tell Steve from marketing to turn it off and on again.
As convenient as they are, remote access VPNs are not as relevant as they once were. Password-protected cloud storage services with zero-knowledge encryption, like Sync.com and pCloud, serve the same essential function. Remote access VPNs can also be hacked through social engineering if passwords aren’t strong enough.
Remote Access VPN Examples:
- NordVPN Meshnet — A free NordVPN feature that can remotely access a corporate network through an encrypted connection to a member device.
- GoodAccess — A cloud-based network resource manager with native apps.
- Citrix Gateway — A single two-way node that enables remote access to business networks while also protecting outgoing communications.
3. Site-to-Site VPN
- Unrestricted link between closed networks
- Can replace a whole communication stack
- Ideal for businesses with multiple locations
- Complicated & expensive implementation
- Passwords still a point of vulnerability
A site-to-site VPN connects two or more closed networks from different physical locations. If a business has several offices, especially in more than one country, a site-to-site VPN is often the easiest way to exchange information between them.
a network, including connecting it to other networks.
A site-to-site VPN works by automatically forwarding traffic between the routers for each site. Any node can access each network as though it’s using the local router. Those who aren’t at one of the sites are still locked out, but they can enter through a remote access VPN. Airlines, hospital networks and other sprawling organizations make use of site-to-site VPNs.
Site-to-Site VPN Examples:
- NordLayer — Nord Security software that manages both remote access and site-to-site VPNs.
- Perimeter 81 — Software that encrypts all corporate traffic and controls access points.
- Twingate — Allows authorized users to automatically connect to corporate IP addresses without manual credential entry.
4. Extranet VPN
- Can access controls for companies that work with outside partners
- Grants different access levels to all points of a supply chain
- Enables coordination across complex businesses
- Hundreds of access points must be carefully controlled
- Mainly cost-effective for large enterprises
- Passwords still a point of vulnerability
An extranet VPN, or site-to-site VPN over extranet, is the next step beyond a site-to-site VPN. Where that type of VPN allows devices on the organization’s closed network to access remote routers as though they were local, an extranet VPN simply broadens that access to outside organizations.
No business, school or agency can stand entirely on its own. The more one grows, the more it depends on third-party vendors and clients. A large enterprise may need to exchange files hundreds of times with everyone from lawyers to freelancers to truck drivers. An extranet VPN lets those people connect to the internal information they need more quickly.

However, the network is still private. The central company controls what every third party can access through the site-to-site VPN. This requires a lot of careful focus, and passwords still need to be strong, of course.
Site-to-Site VPN Over Extranet Examples:
- Zscaler Private Access — Allows access to specific apps on a system with fine-grained control.
- Palo Alto Networks GlobalProtect — Comes with Android and iOS apps so mobile devices can easily access the network.
- Cisco Dynamic Multipoint VPN — An enterprise VPN that achieves high speeds and low latency by balancing loads across the entire corporate system.
The Most Common Types of VPN Protocols
| Protocol: | Encryption | Pros | Cons |
|---|---|---|---|
| OpenVPN | AES-GCM-256 | Open-source & stable | Large attack surface due to more code; TCP can be slow |
| WireGuard | ChaCha20 | Open-source, secure & very fast | Newer & untested |
| IKEv2/IPsec | AES-256 | Fastest available connections | Owned by Microsoft & Cisco |
| SSTP | AES-256 | Secure & hard to block | Owned by Microsoft |
| L2TP/IPsec | AES-256 | Broadly compatible with various apps | L2TP is not secure on its own |
| PPTP | RC4 | Fast | No longer considered secure |
| Proprietary Protocols | Many types | Often very fast & secure | Normally exclusive to one VPN service |
Whether they’re managing access to an entire U.S. government department or helping one guy in Toronto stream ‘Shogun,’ VPNs tend to use the same set of protocols. A protocol is a set of instructions that let VPN servers talk to other servers and clients, even if no relationship has been configured between them.
In this section, I’ll talk about the most common protocols you’ll encounter on any type of VPN and explain how to choose one. Before I start, you may notice that SSL and TLS don’t come up — that’s because they’re not VPN protocols, but tools for authenticating web requests. SSL is nearly obsolete, and TLS is always used in conjunction with one of the protocols below.
OpenVPN
- Generally fast & stable
- Two transport protocols
- Open-source
- Larger codebase is more vulnerable
- UDP may drop connections
- TCP can be slow
OpenVPN is the meat-and-potatoes protocol that has allowed the VPN sector to flourish in the last decade. Being completely open-source, it’s the heart of a dedicated community that combs its code looking for any vulnerabilities. As you can see from this list of security advisories, these white hats are great at catching flaws before the bad guys do.
OpenVPN works with two transport protocols. Transmission Control Protocol (TCP) produces more stable connections, while User Datagram Protocol (UDP) is usually faster. These two settings make OpenVPN the Swiss army knife of protocols. No matter what you’re doing, it’s almost never a bad choice.
WireGuard
- Very fast connections
- Hard to attack
- Open-source
- Logs IP addresses by default
- Needs more evaluation
WireGuard is the newest VPN protocol that’s not exclusive to one service. So far, the consensus is that it’s faster and more stable than OpenVPN, making it the ideal choice in most situations. It’s also open-source, and in my experience, the hype is well earned. I use WireGuard by default unless I’m on ExpressVPN or NordVPN, which have their own implementations.
WireGuard has one Achilles’ heel. It gets its speed from creating stable connections between servers, avoiding the need to authenticate every connection individually (which can slow down OpenVPN). This requires it to temporarily log IP addresses that may then be vulnerable if the server is breached. Luckily, the top VPNs use RAM-only servers to wipe these addresses hourly.
IKEv2/IPsec (Internet Key Exchange version 2/IP Security)
- Good for moving between mobile networks
- Often the fastest connection
- Uses a port that can be blocked
- Not open-source
The key advantage of IKEv2 is speed. Its architecture keeps both speed and latency low. For the same reason, it excels at picking up connections after one drops, especially on a mobile device moving between networks. The main drawback is that IKEv2 is not open-source, with code jointly owned by Microsoft and Cisco. It’s hard to verify its overall safety.
IKEv2 is one of two protocols that use Internet Protocol Security (IPsec) for part of their security. IPsec creates a secure association between two servers, but only when it’s been set up on both of them — this makes it a common choice for remote access and site-to-site VPNs. IKEv2 allows it to talk with unsecured servers, so you’ll find it on a lot of personal VPN apps.
SSTP (Secure Socket Tunneling Protocol)
- Easy manual setup on Windows
- Secure default encryption
- Very hard to block
- Requires user authentication
- Owned by Microsoft
- Can be slower
SSTP was developed by Microsoft, which still has sole rights to its source code. Microsoft developed it to replace PPTP, and SSTP does have several advantages over that deprecated protocol. It uses secure AES-256 encryption by default and accesses the same port as HTTPS traffic, making it extremely hard to block without cutting off the internet altogether.
Though it has some benefits, SSTP is rarely seen these days, especially outside of devices running Windows. Where other protocols support automatic client authentication, SSTP requires more labor-intensive user authentication, which also makes it slower. While generally secure, SSTP isn’t particularly convenient.
L2TP/IPsec (Layer 2 Tunneling Protocol/IP Security)
- Integrates with several security protocols
- Natively supported on most devices
- Slow & easily blocked
- Outdated
L2TP, one of the oldest VPN protocols, is not secure by itself. As with IKEv2, it’s almost always paired with IPsec, but there’s one difference. With IKEv2, IPsec just handles authentication, while for L2TP, IPsec is responsible for all encryption and security. This makes its use of port 500 a bigger risk, since its traffic is easier to block.
L2TP’s flexibility has given it a lot of staying power. It’s easy to implement on all devices and operating systems, and it can work with more security protocols than just IPsec. However, setup is cumbersome compared to more modern protocols, and options without inherent encryption just don’t cut it anymore. Most VPNs have phased out L2TP by now.
PPTP (Point-to-Point Tunneling Protocol)
- Relatively fast
- Based on an obsolete cipher
- Not secure
I won’t waste your time: Don’t use PPTP. This old-school VPN tunneling protocol was once high VPN technology, but today it’s so dated that I dock points from VPN services just for offering it. PPTP’s default security is called Microsoft Point-to-Point Encryption (MPPE), which is based on the RC4 cipher — an algorithm so old that its successor, RC5, has also been cracked.
PPTP is fast, but that speed is part of the problem, indicating its lack of a secure tunnel. It may cut it if you’re just changing your IP address for streaming, but there’s no use case for PPTP that WireGuard or IKEv2 can’t handle better. Steer clear.
Proprietary VPN Protocols
- Add value to a VPN when well-made
- May be optimized for specific tasks
- Often very fast & stable
- Only available on certain services
- Don’t always offer any advantages
- Rarely open-source
Certain VPNs come with protocols you can’t find anywhere else. Sometimes, as with ExpressVPN’s Lightway, the team behind the VPN built the protocol from scratch. In other cases, such as NordVPN’s NordLynx, the protocol is based on an existing open-source codebase like WireGuard.
All three of the proprietary protocols above are great performers, but proprietary protocols can’t always be trusted. For example, I found that Hotspot Shield’s Catapult Hydra protocol — despite its outstanding name — leaked DNS requests and exposed my real IP address. I’ve yet to see an exclusive protocol convince me to subscribe to a VPN I didn’t already trust.
Conclusion
Unless you’re the head of IT for a medium-sized organization or larger, you’ll most likely only deal with the first two types of VPN that I covered: VPN apps and remote access VPNs. The former can help you do anything, from banking securely to enjoying foreign TV, while the latter provides a convenient solution for remote work that’s becoming increasingly common.
However, in a world ruled by information architecture, it’s never a bad idea to know more about your surroundings. The next time you’re called to access a closed network, you’ll be ready to use the local VPN without breaking a sweat. In the meantime, you can enjoy movies, music, worldwide gaming and international shopping deals from personal VPNs.
Which of the four types of VPN have you used? Do you have any stories of VPNs saving the day in your workplace? Did I leave anything out of this discussion? Let me know in the comments, and of course, thank you for reading!
FAQ: Types of VPNs
Which VPN Tunnel Style Routes Only Certain Types of Traffic?
Split tunneling is the common term for a VPN feature that routes some traffic through an encrypted server while leaving other traffic unprotected. It’s useful for sites or apps that are impossible to use with a VPN connection.What Types of Encryption Does a VPN Have?
Most modern VPNs use AES-256, the current gold standard for encryption, which is also used by the U.S. government and most banks. Some protocols use the equally secure ChaCha20 stream cipher instead.How Does a VPN Provide Additional Security Over Other Types of Networks?
A VPN encrypts all communications leaving the user’s device, then sends them on to be decrypted at the VPN server. This encrypted “tunnel” ensures nobody can trace the signal back to its source or spy on it in transit.What Are the Three Most Common Types of VPN Protocols?
The vast majority of today’s VPNs use either OpenVPN, WireGuard or IKEv2/IPsec. All three VPN protocol options are secure, though the latter two are faster, and only the former two are open-source.

Leave a Reply