What Is SSH Tunneling and How It Works Explained in 2025
Quick Summary: What Is SSH Tunneling?
SSH tunneling, which stands for Secure Shell tunneling, establishes an encrypted channel between a client on your end and a server near your destination. You can safely exchange data through this conduit, even if the devices on either end don’t natively support encryption.
SSH tunneling is a double-edged sword. You may have heard that it’s a key tool for complying with data privacy laws, or a nefarious weapon of hackers and ransomware groups. In truth, like all encryption, SSH tunneling is just technology that can be used or misused.
In this article, I’ll tell you all the facts about this ubiquitous but risky security software.
What Is SSH Tunneling?
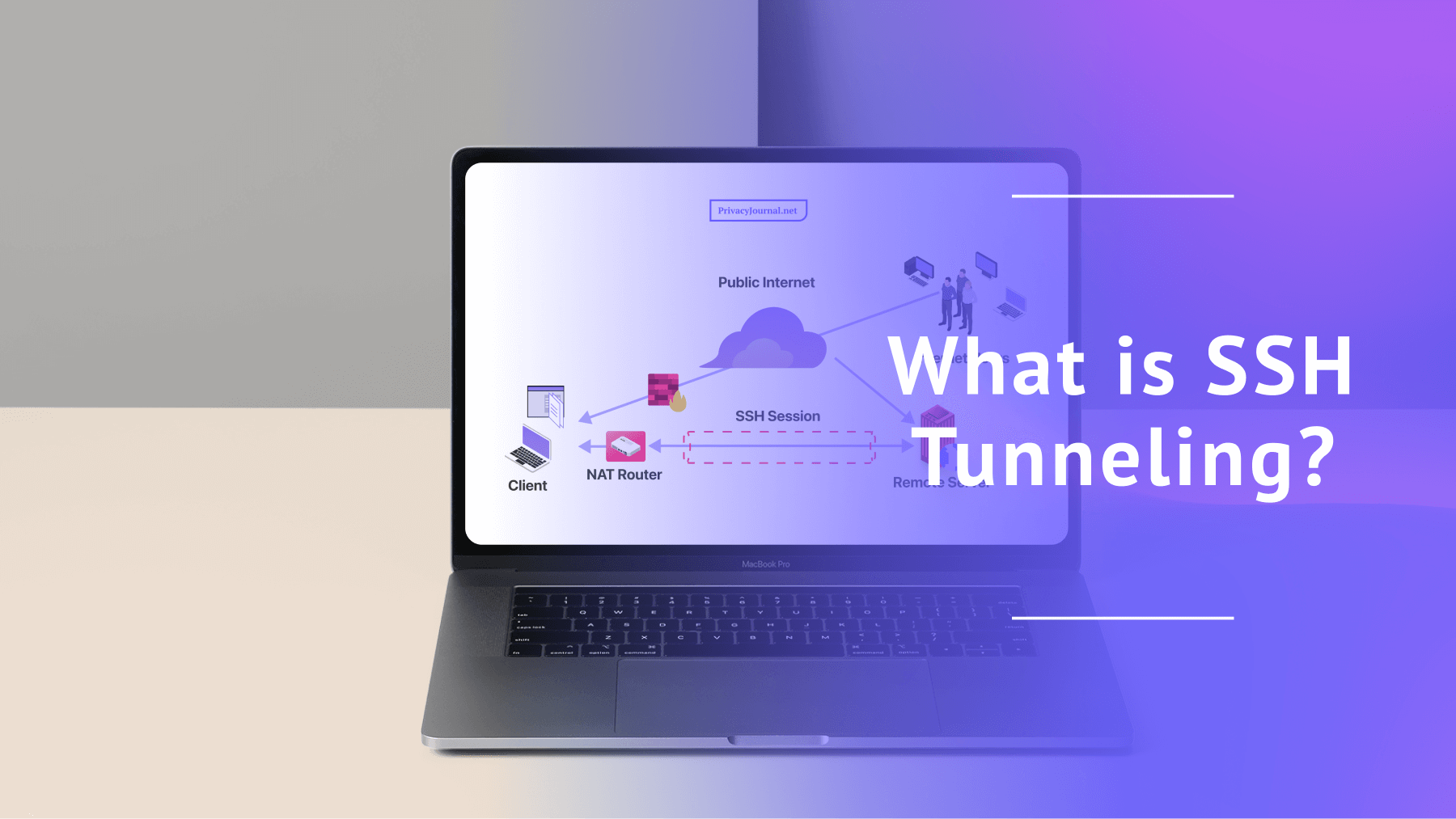
SSH tunneling is a method of creating a secure channel between two devices, even if those devices weren’t originally built for encrypted communication. A secure channel is a pretty simple concept: Information gets encoded on one device and isn’t decoded until it reaches its destination. Anyone who tries to view it en route won’t be able to read it.
SSH, or Secure Shell, is all-purpose software for exchanging information safely across public channels. It has tons of use cases, from managing public servers to providing passwordless logins, but today I’m focusing on how it can securely exchange data across the public internet. It does this through a form of local port forwarding.
In general, port forwarding occurs when connections hit a router and are sent to specific destinations on that router’s network. SSH tunneling uses port forwarding to send inbound and outbound communications through the SSH tunnel. Boom — safe data exchange.
SSH was invented in 1995, which makes it a fossil by internet standards — but sometimes, you can’t beat the classics. There’s a reason why IT professionals and hackers alike still use “SSH” as a verb; as a low-overhead security solution, SSH tunneling has outlasted almost all its rivals.
How Does SSH Tunneling Work?
To set up an SSH tunnel, an SSH client will securely connect with an SSH server and automatically send all traffic along that secure route. If you know how a VPN works, you’re already well on your way to understanding SSH tunneling — data is encrypted when it leaves your device and decrypted once it gets where it’s going.
The big difference between a commercial VPN and SSH is that an SSH tunnel will communicate with a specific server, not the whole internet. The process looks like this:
- An SSH client app (installed on your home device or router) connects with an SSH server, usually on the same machine as the destination server.
- The SSH tunnel communicates with a specific access port on your device. To send data securely to the destination, the SSH client just has to forward outbound requests to that access port.
- The port sends requests through the tunnel to the SSH server, which decrypts them and sends them on to the destination server.
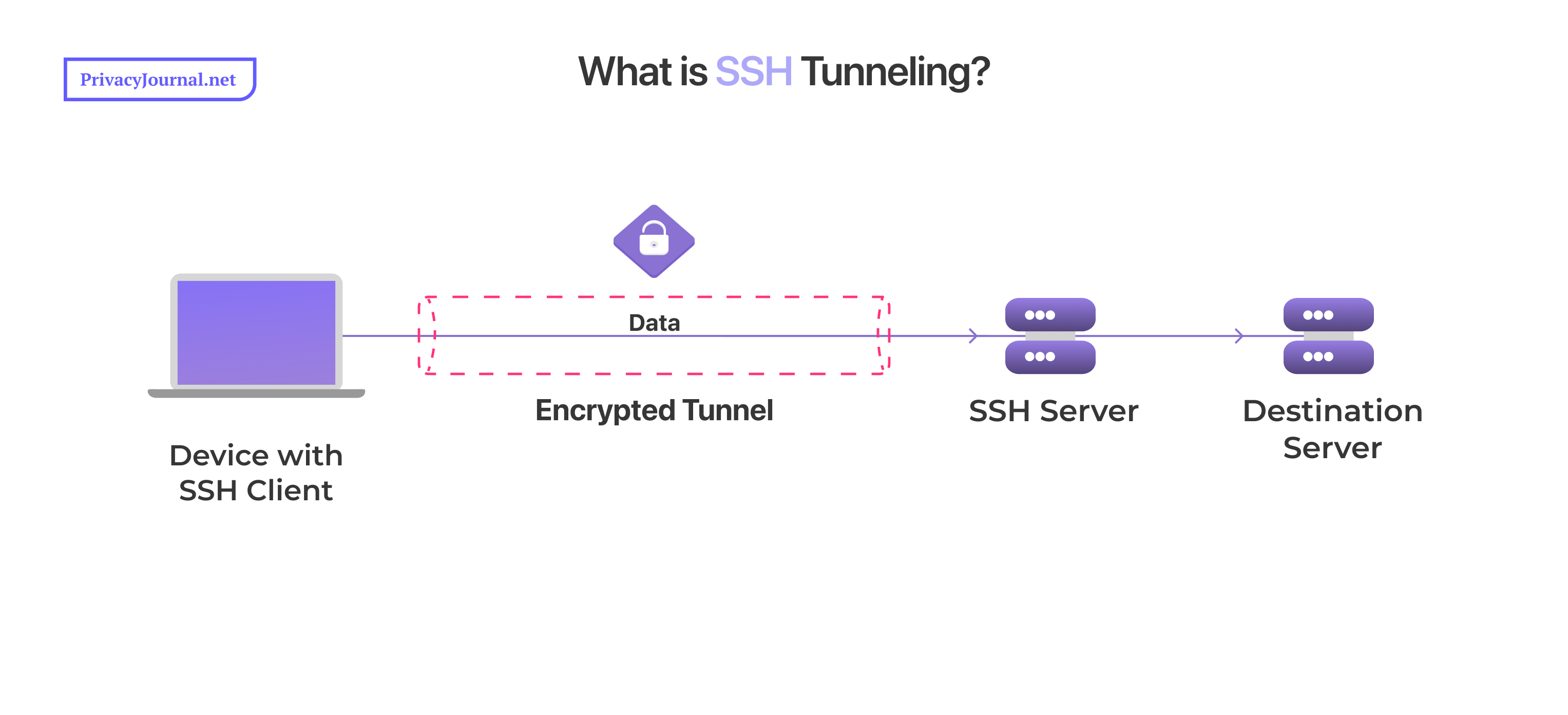
destination instead of opening onto the whole internet.
SSH Tunneling vs Port Forwarding
As I’ve mentioned, SSH tunneling is a kind of port forwarding. You can think of port forwarding as a building receptionist. When you walk into the lobby, the receptionist can tell you what floor and room to go to, which saves you a lot of wandering around. They can also approve your security clearance so you don’t get stopped at a checkpoint.
In this analogy, the lobby is a network router, the rooms are devices on the network, and the security checkpoint is your firewall. Port forwarding speeds up connections by getting data where it needs to go. Also, access that comes through port forwarding can be escorted across the firewall, which might otherwise make it impossible to connect.
SSH tunneling relies on port forwarding to get traffic to and from the SSH tunnel. When selected data leaves your device, your SSH client forwards it to the port where the SSH tunnel begins. In the other direction, responses coming from the SSH server can be sent from the port back to your device.
If you’re interested in personal access to port forwarding, I’ve written an in-depth ExpressVPN review covering the best VPN service that includes it.
What Is Reverse SSH Tunneling?
Reverse SSH tunneling is a way to safely move web traffic from the public internet to devices behind your firewall. Depending on how your remote access is set up, you may encounter situations where you can access an SSH server but not its associated client. This usually happens when the server is on the internet, but the client is on a secure network.
You might also see reverse SSH tunneling called remote port forwarding; they’re the same thing. It’s called “reverse” because you connect to the server first, then go through the SSH tunnel to reach the client. As usual, port forwarding directs your data from the SSH client machine to the device you’re trying to reach.
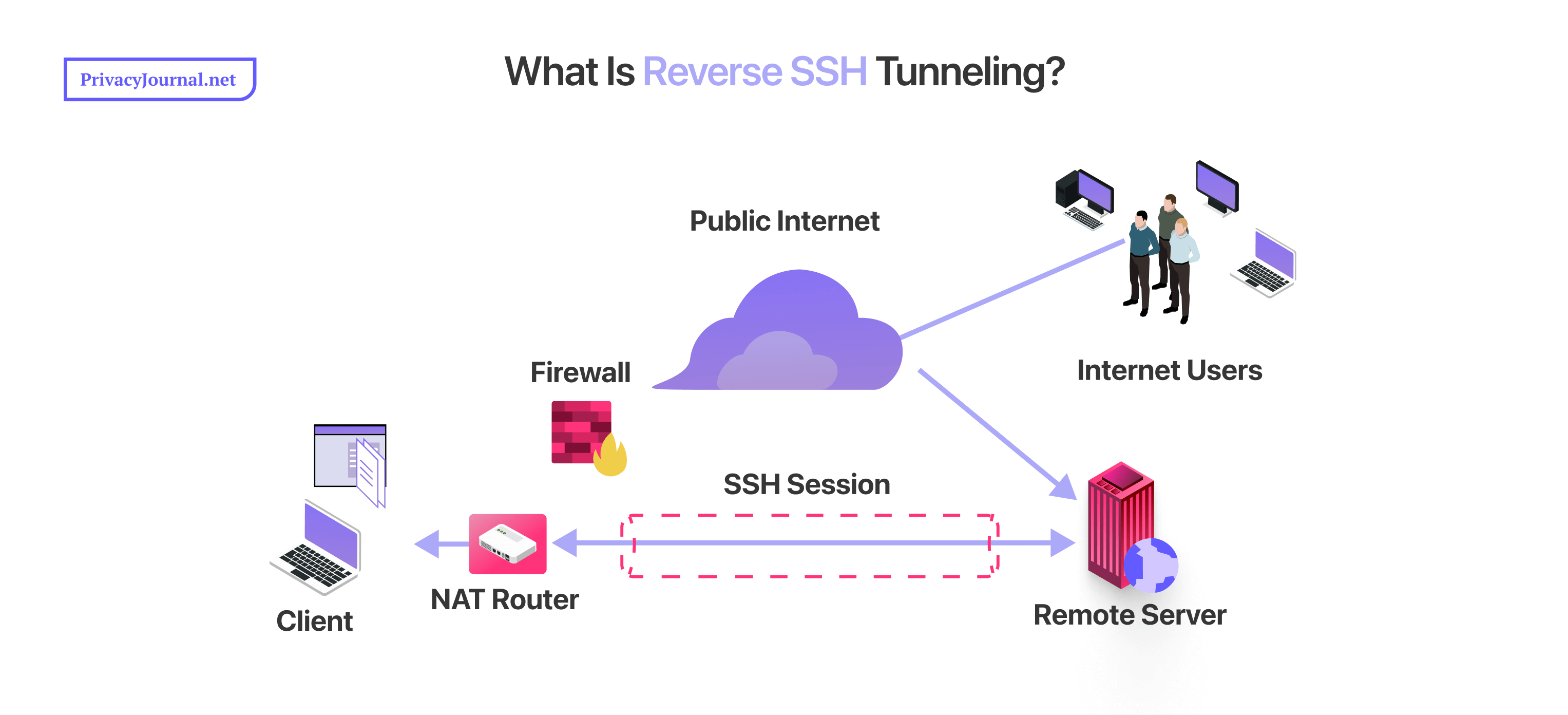
available only on private networks behind firewalls.
Reverse SSH tunneling comes in handy whenever you have to remotely access a personal computer. It can secure remote desktop protocols, file transfers, or private gaming and media servers. If you’re dealing with a particularly strict firewall, SSH reverse tunneling might be the only way to connect at all.
What Is SSH Tunneling Used For?
The beauty of SSH tunneling is that it can secure applications and devices without overhauling them. It’s similar to many types of VPN connections, but demands less work to install. I’ll run through an example of how this can be a lifesaver.
Imagine you work at a clinic that’s part of a family of hospitals. Each hospital in the network stores patient information in a central database; every day, you use a work computer to check charts stored in the main data center. However, that center’s software was built in the early ’90s and doesn’t support encryption.
If you keep exchanging patient info across unsecured channels, you risk violating HIPAA. But revamping the whole data mainframe to encrypt outbound communications could paralyze half a dozen hospitals for weeks.
SSH tunneling provides a much simpler solution. Instead of laboriously rebuilding legacy software, the hospital network’s IT department can set up SSH servers at the data center, then install SSH clients on clinic computers. This builds a secure tunnel atop the existing software — no need to rip anything out at the roots.
Who Needs SSH Tunneling?
SSH tunneling is for anybody who must connect remotely and securely to any device on a regular basis. As I covered above, it’s ideal for companies that want to secure their connections without rebuilding their software, but it’s also a great way to leave a port open for general access without compromising security.
In the section on reverse SSH tunneling, I explained how an SSH tunnel can make web services publicly accessible without making your entire private network vulnerable. If your workforce regularly uses private databases or internal web apps, SSH tunneling can ensure safe access to those resources.
You can also use SSH tunneling for remote automatic backups, encrypting data before sending it to or from your backup servers. It’s even got applications outside of work — for example, you can use a reverse SSH tunnel to hop on a friend’s private gaming server without leaving it open for everybody.
Advantages and Disadvantages of SSH Tunneling
In the intro, I alluded that SSH tunneling has both benefits and risks. Although it’s a groundbreaking security apparatus, its secrecy can always be misused. Let’s explore the pros and cons.
Benefits of SSH Tunneling
I’ve covered a lot of what SSH can do for you, but here’s a summary.
- Tunnels offer an easier way to secure systems. You don’t have to throw out the legacy software your organization relies on — SSH tunneling can be layered on top of what you already have.
- You can leave ports open securely. An SSH tunnel ensures that an open port won’t leave your entire network unguarded. Any traffic that reaches the port is sent straight through the tunnel.
- Tunnels make your networks compliant. Without security measures, your remote connections might violate data privacy laws.
- They provide more precision than a VPN. Although SSH tunnels and remote access VPNs cover many of the same use cases, it’s much harder for the end user to configure split tunneling on a VPN, while SSH tunnels sort traffic by default.
Drawbacks of SSH Tunneling
Malicious actors can also make use of SSH tunneling, so it’s important to think carefully about their vulnerabilities.
- Tunnels can serve as backdoors into your network. If a hacker gains any sort of access to your system, they can set up a tunnel between your servers and their own devices. Since SSH port forwarding crosses the firewall, they’ll be able to come and go as they like.
- Tunnels can also conceal illicit activities. Encryption makes it so nobody can see what passes through an SSH tunnel — not even the network’s own administrators. If a ransomware attacker uses an SSH tunnel to siphon off your sensitive data, you may not discover it until it’s too late.
SSH tunneling is safest when used alongside other security measures, like careful access controls, physical device security, multi-factor authentication and strong passwords. It combines pretty seamlessly with NordVPN Meshnet, which is a great way to add redundant security layers.
How to Set Up SSH Tunneling
The specific setup procedure varies a lot based on your operating system and SSH implementation, so out of necessity, this will be a brief overview.
- First, you’ll need to create an SSH server-client pair. Log in to the OS of your intended remote server and install an SSH implementation — OpenSSH is popular and easy to use. This will allow you to create an SSH connection into that remote machine using its IP address or URL.
- Next, on the device you’ll use for access, install the client for the same implementation. Open the terminal on the client device.
- From here, the proper command will vary by operating system. Replace the terms in square brackets with the appropriate word (note that these steps both assume you’re using OpenSSH).
- On Windows PowerShell, enter “ssh [domain]\[username]@[servername],” then enter “yes” to make that server known to your client.
- On the macOS terminal or Linux shell, enter “ssh -L [local port]:[destination server IP]:[destination server port] [username]@[SSH server URL or IP].”
- After each step, enter your user password for the destination server to finish the connection. You’ll now be able to pull data from that server through an SSH tunnel.
Conclusion
You may not need to use SSH tunneling regularly unless you’re directly involved in IT or security at your job. But if you ever work remotely or access off-site resources, it’s a useful tool to add to your chest. If you can set up a quick SSH tunnel, you’ll have more options to securely connect with the data you need to do your job.
I hope this article has helped you better understand what SSH tunneling is and why it’s important. If you have any further questions, leave them in the comments, and I’ll do my best to respond. Thanks for reading!
FAQ: SSH Tunneling Explained
What Is Tunneling in SSH?
SSH tunneling is when you communicate with a remote server via an SSH client on your internal network and a paired SSH server on a remote network. All data passing between the paired devices is encrypted.Is an SSH Tunnel Like a VPN?
An SSH tunnel and a VPN both create a secure connection to a remote asset, but an SSH tunnel is configured between two specific devices, while a VPN uses one server to access an entire network.How to Create a SSH Tunnel?
Install an SSH server on or near the same device as your destination server, then install a client from the same implementation on your local machine. After that, the universal command formula is ssh -L [local port]:[destination IP]:[destination port] [username]@[SSH server URL or IP].Is SSH a Tunneling Protocol?
SSH, or Secure Shell, is a full suite of security tools — including the SSH protocol, which you can use to establish secure tunnels.

Leave a Reply