
How to Set Up a VPN for Remote Access: A Guide for Windows Users in 2025
Quick Summary: How to Set Up a VPN for Remote Access
A remote access VPN secures your connection to a private network through encryption, allowing you to access sensitive data safely from anywhere. NordLayer is the best VPN for remote access; try it with a 14-day money-back guarantee.
A remote access VPN is used to create a secure tunnel between a network and a remote user, preventing unauthorized parties from intercepting data. Unlike our best VPN picks, which are designed to keep individuals safe online, remote access VPNs create an encrypted tunnel to another private network. In this article, I’ll show you how to set up a VPN for remote access.
Before we start, I recommend looking over our guide to the types of VPNs. You can install personal VPNs quickly on any device, but setting up a VPN for remote access isn’t that simple. You’ll need a VPN client, a VPN router, a gateway and a host of manual configurations before you can get it working. In this article, you’ll learn how to do just that.
What Is a Remote Access VPN?
A remote access VPN is a virtual private network that’s used to remotely connect multiple devices to a private network. It’s a convenient digital security solution that lets many remote workers access a password-protected company network from any location without the risk of sensitive corporate data getting intercepted by third parties.
Regular VPNs and remote access VPNs provide similar levels of security as both generally offer AES-256 encryption, but their core functions are different. A regular VPN — like the one we cover in our NordVPN review — connects you to a public web server. It masks your IP address and encrypts the data that’s transmitted between your device and the server.
On the other hand, a remote access VPN connection gives you access to a specific private network through a predetermined server. This lets you connect to that particular network from any location using a remote desktop solution, so you can avoid the risk of malicious players intercepting your traffic and causing damage.
Most remote access VPNs also incorporate Zero Trust Network Access (ZTNA) into their security framework. ZTNA is a security solution that offers extra countermeasures for cyber threats, like multi-factor authentication or single sign-on options. These airtight verification methods make it harder for anyone outside the protected private network to gain access.
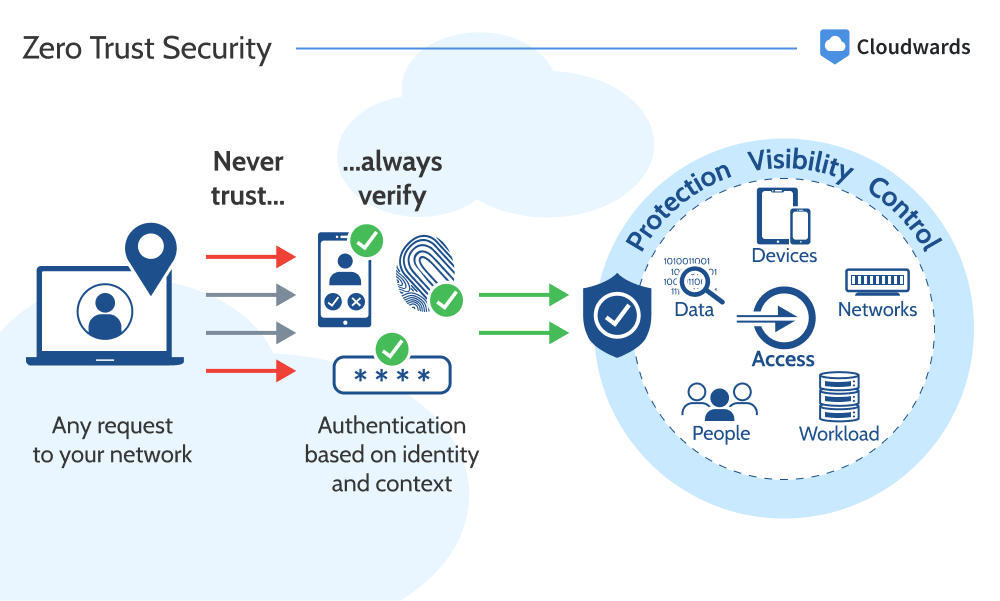
A remote access VPN isn’t ideal for performing regular VPN functions, like gaining access to geo restricted streaming sites, but it does offer benefits for organizations. Firstly, it enables people to work remotely through a secure channel. Secondly, it protects the internal network by making it extremely difficult for anyone but an employee with login credentials to access the network.
Thirdly, remote access VPNs use Zero Trust Network Access (ZTNA) safeguards like multi-factor authentication and single sign-on, among many others. These options let the organization’s managers control who can access vital resources. By extension, this limits the chances of the wrong person gaining access to the private network.
Even if hackers find a way to compromise one device, having secure access in place means they can’t use it to attack the rest of the network without a new authentication. You can reach the business VPN on anything with internet access, from mobile devices to desktop operating systems.
However, like any security tool, remote access VPNs aren’t entirely foolproof and are still vulnerable to social engineering attacks. They’re also ineffective against an inside attack from a malicious employee. Preventing these attacks involves processes that are aimed at establishing trust before any employee is given sensitive access privileges.
How a Remote Access VPN Works
A remote access VPN works by combining a number of resources.
First, you’ll need a VPN client that uses secure protocols like OpenVPN and WireGuard. NordLayer or Cisco AnyConnect are some examples of software you can use to set up secure remote access. The protocols that the VPN client provides will determine the type of encryption applied to the targeted traffic. We discuss how that works in our VPN protocols article.
The second thing you need is a VPN gateway, which is a router or dedicated server located within the secured business network. Its main function is to authenticate the VPN client when it tries to establish a secure connection. A commonly used VPN gateway for remote access VPNs is the Routing and Remote Access Service (RRAS), a Microsoft API.
The final important piece is an authentication mechanism for verifying the user credentials of any remote users on the secured network. This is usually built into the VPN gateway and managed through it. Active Directory by Microsoft is one example of an authentication service used for managing remote access VPNs.
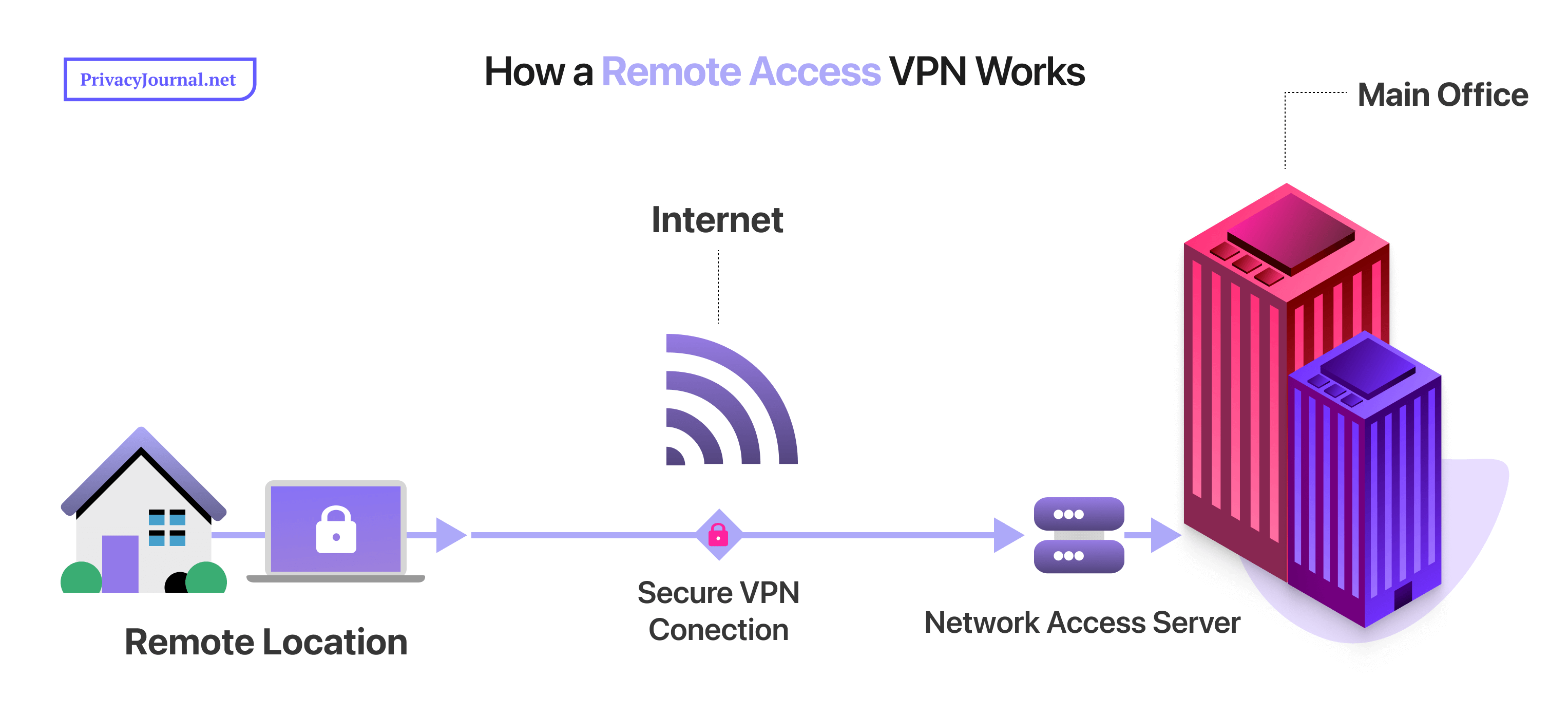
Once everything is set up, the remote employee can launch the VPN client provided by the organization and enter their login credentials. The VPN client then sends the user’s credentials to the VPN gateway/server for verification.
Once the user has been verified, a connection is established with the VPN server’s owner, who chooses the encryption protocols to use. This becomes the default for every connection that’s established afterward. Any data that gets transmitted through the server will be encrypted, making it hard for an outsider to intercept it.
The remote user can now securely access all the areas of the private network, as far as their credentials permit them. They can remotely access network resources like internal websites, databases, file servers and more.
Step by Step: Setting Up a VPN for Remote Access
You can set up any device as a remotely accessible VPN server, but you’ll usually need third-party software to make it work. However, Windows 10 and 11 let you turn a computer into a VPN server without needing any extra service.
Windows 10 and 11
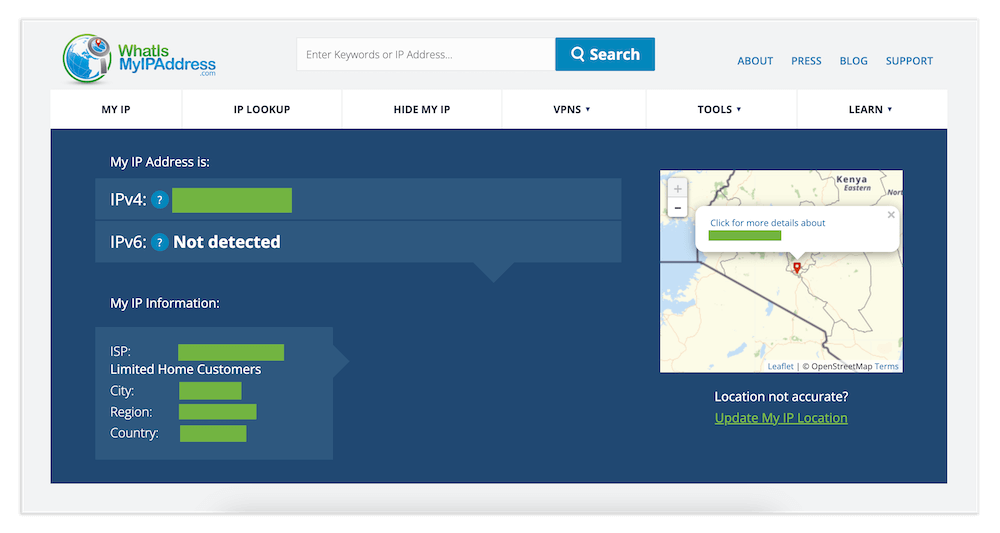
1. Find Your IP Address
First, you need to determine what your IP address is. This is a unique string of numbers assigned to you by your internet service provider. You’ll need this IP address to contact your VPN server remotely. There are several online resources like WhatIsMyIPAddress that you can use to find your IP address.
2. Configure Port Forwarding on Your Router
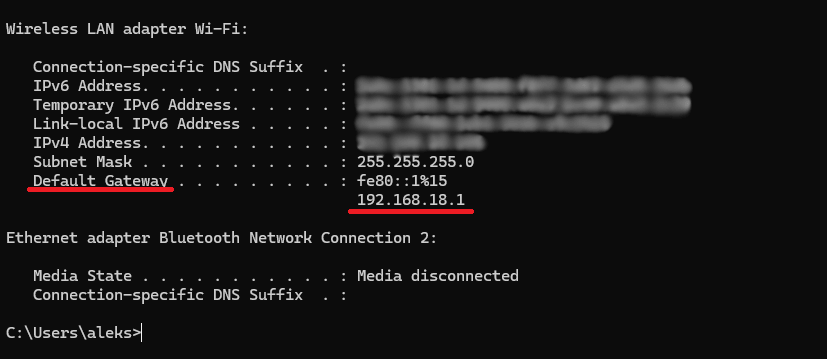
You need to port forward the Secure Socket Tunneling Protocol (TCP port 443) to allow your home VPN server to connect to a public network. Open your router web page interface by typing the router’s IP address into the search bar.
Note that this is not the same as the IP address you found in step one. You can find this IP address printed on the back of your router or by opening the Windows Command Prompt, typing the command “ipconfig” and looking for the address called “default gateway.” It usually looks something like 192.168.0.1.
Enter your username and password, which can both be found at the back of your router (unless you’ve manually changed them). Then turn on port forwarding in your router’s control panel. The actual location of the “port forwarding” setting varies depending on your router’s model and firmware. If you can’t find it right away, check the help page for your specific router.
3. Launch the Control Panel
Open the Control Panel and click “network and sharing center.” Then click “change adapter settings” on the left panel of your screen.
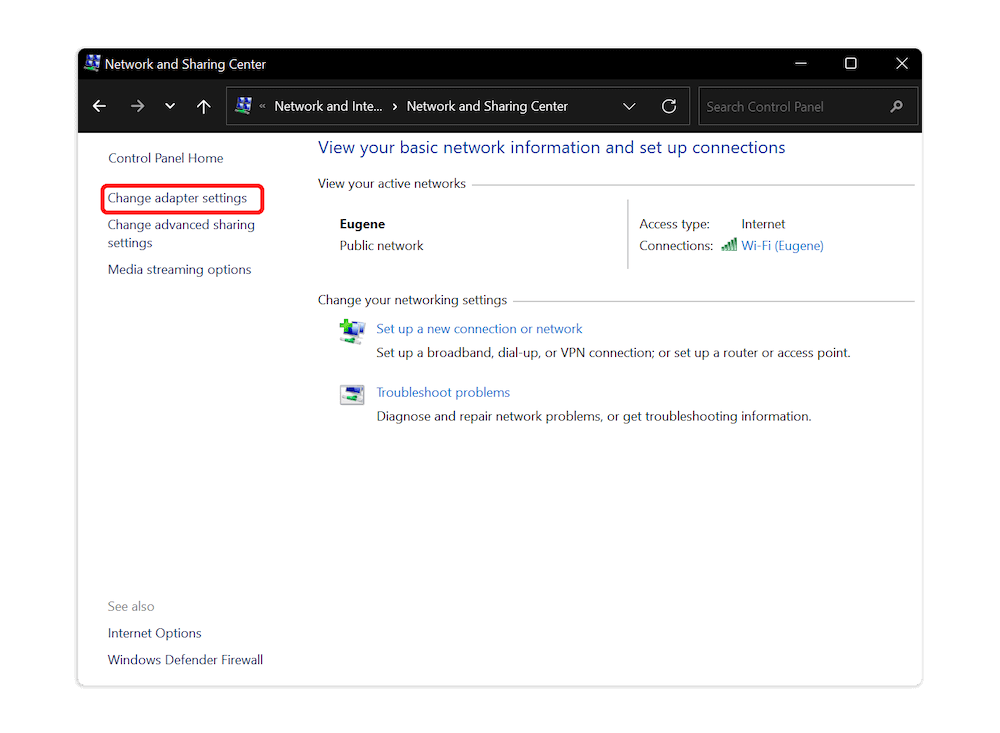
4. Set Up a New Incoming Connection
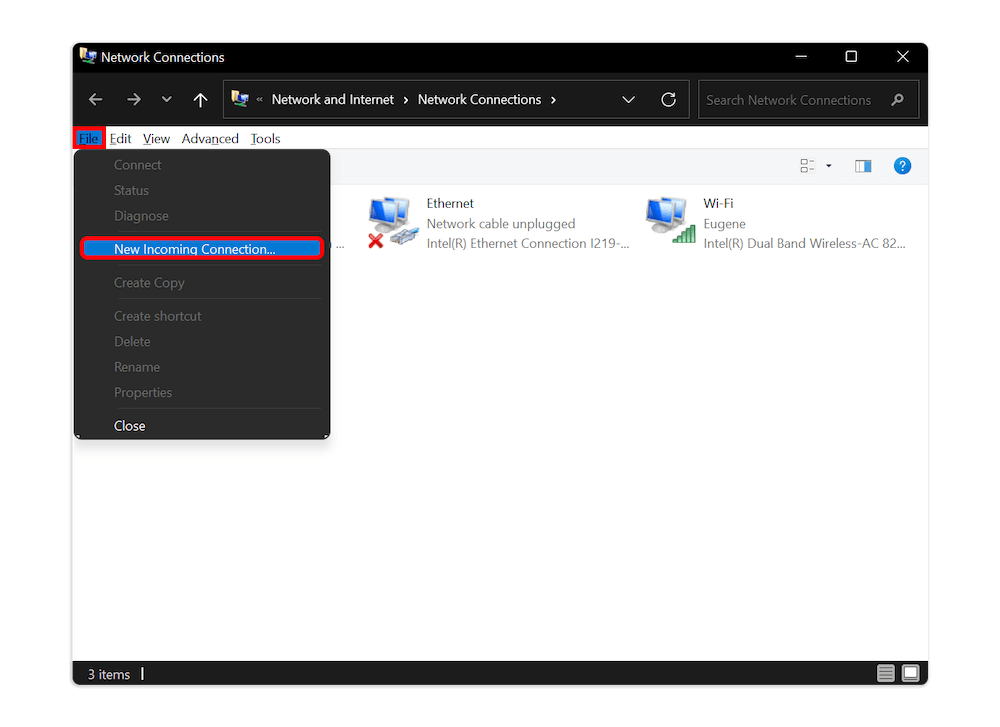
You should now be on the “network connections” page. On the menu tab, click “file” and select the “new incoming connection” option. If you don’t see the menu tab, press the Alt key once to make it visible.
5. Select the Users
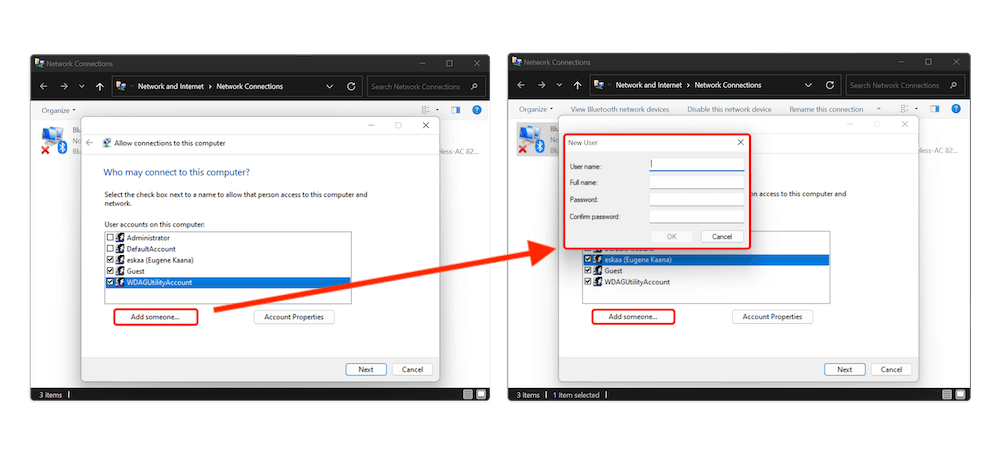
You’ll be directed to an “allow connections to this computer” window. Here, you can manage which users on this computer will have access to the VPN server you’re configuring. Once you have selected these users, click “next.” Then click the “add someone” button and finish by clicking “OK.”
6. Choose the Connection Path
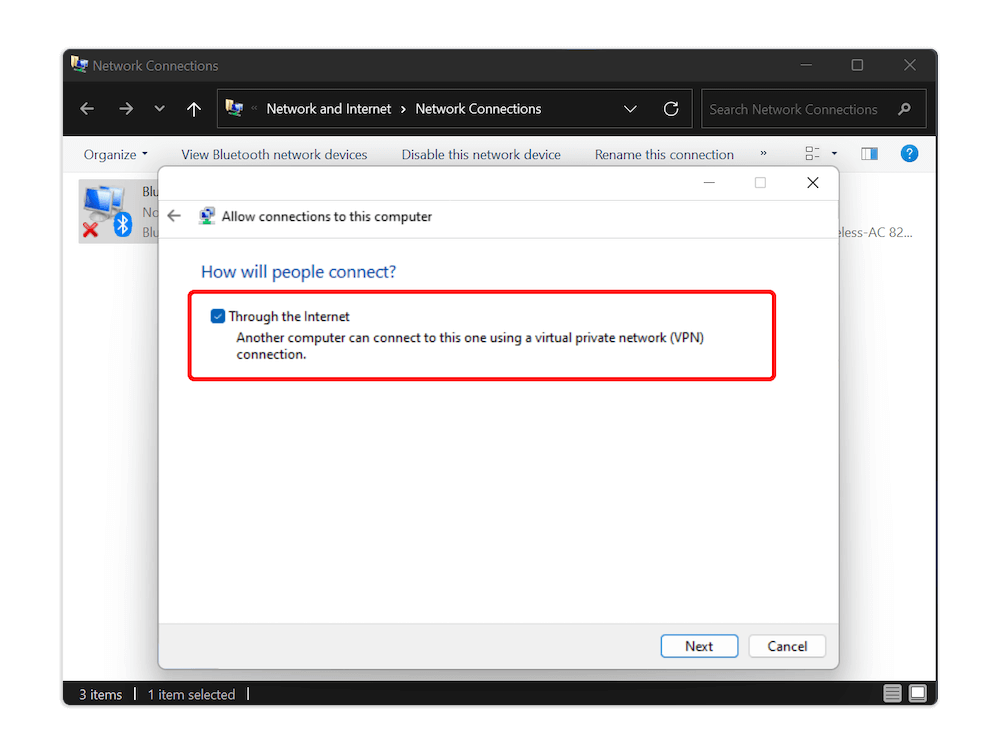
You’ll be directed to another page where you must choose how people will connect to the VPN server. Check the box next to the “through the internet” option and click “next.”
7. Select TCP/IPv4
On the page that appears, select Internet Protocol Version 4 (TCP/IPv4) and click the “properties” button.
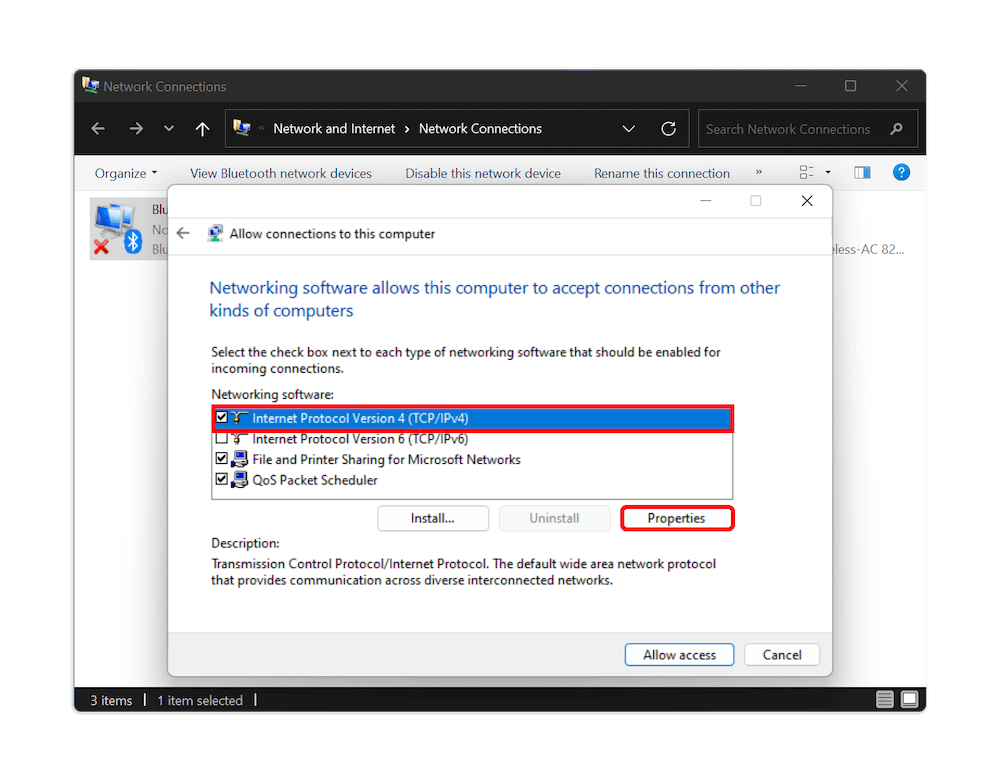
8. Specify the IP Addresses
In the small window that appears, check the box next to “allow callers to access my local area network.” Under the IP address assignment, select “specify IP address” and set the number of clients who can access your VPN server at once. You can find the possible range in the “settings” page on your router control panel.
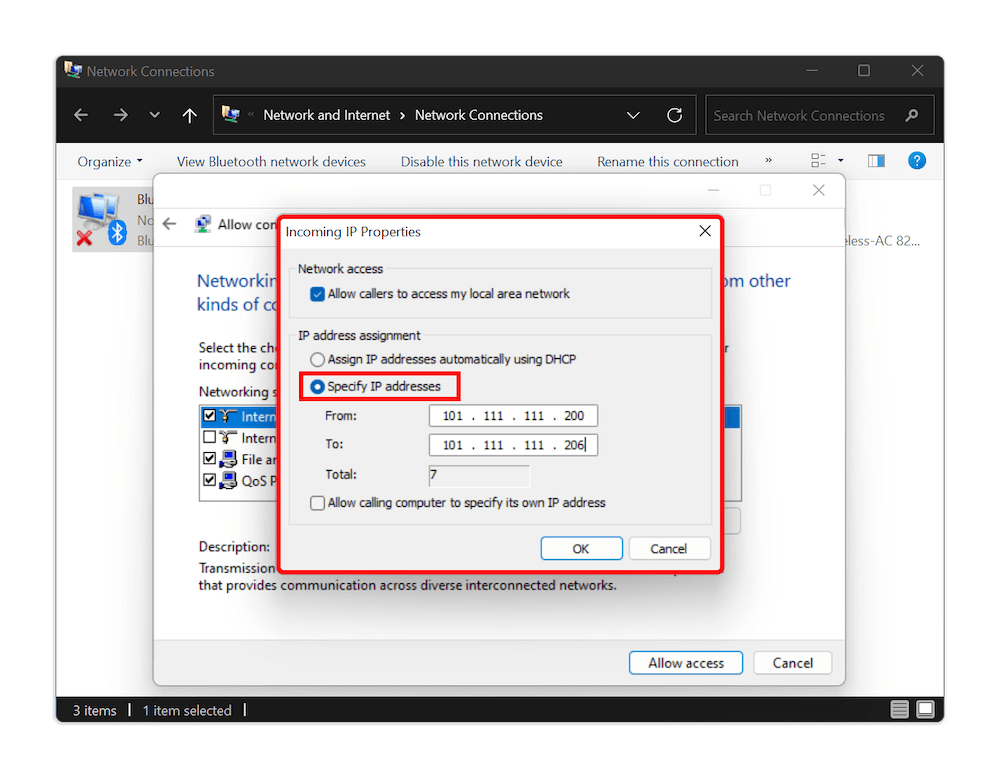
9. Create the VPN Server
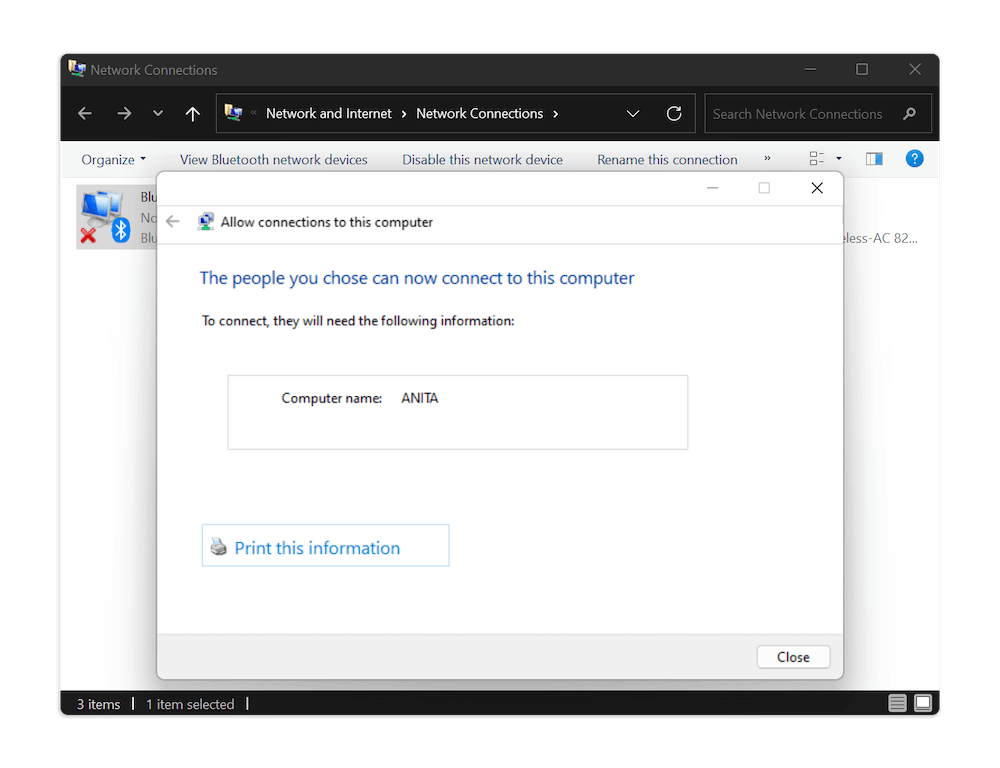
Click the “OK” button and then click the “allow access” button. Finish by clicking the “close” button. You have now created a VPN server. The final step is to ensure that the firewall will let your remote connections through.
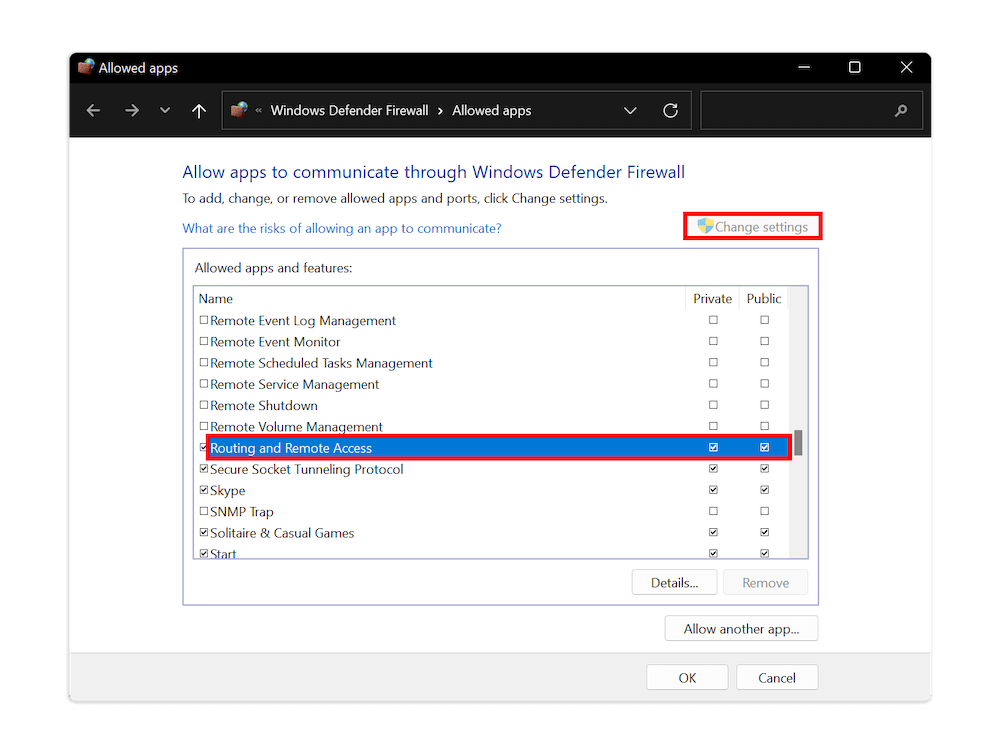
10. Configure the Firewall to Allow VPN Connections
Click the “start” icon. Search for “allow an app through Windows Firewall” and choose the first result. Select “change settings” and then scroll down until you see the “routing and remote access” option. Ensure that the “private” and “public” boxes are checked. Click “OK” to complete the setup. The VPN server is now ready for remote access.
Best VPN for Remote Access
As you have already seen, you can set up a server as a remote access VPN, but the process can be cumbersome across a large corporate network. If you’re protecting the resources of a whole business, it’s much easier to find a trustworthy remote access VPN provider. The following are the three best VPNs for remote access.
1. NordLayer — Best VPN for Remote Access
- Fast servers
- Multiple security features
- Secure verification processes
- Best features limited to expensive plans
NordLayer offers multilayered security that prevents all your important resources from being exposed to external threats. This service is part of Nord Security, which also owns NordVPN — see our NordVPN review for details on that personal VPN service.
NordLayer offers high-speed 1 Gbps servers for the smooth transfer of huge files between devices. Encryption protects the transmitted data from being intercepted by anyone outside the network.
It also aligns with the Zero Trust Network Access best practices by providing connected users with multi-factor authentication, biometric authentication and single sign-in options for verification.
Setting up NordLayer is also easier than most alternatives — you need only about 10 minutes to get it running. All you have to do is install the NordLayer app, log in with your organization ID and choose the organization gateways to connect with your device.
2. Perimeter 81 — Best for Large Organizations
- Reliable security features
- Secure verification procedures
- Suitable for large organizations
- Costlier than most alternatives
Perimeter 81 is another reliable remote access VPN that’s best suited for larger organizations. It can be scaled up pretty fast without creating vulnerabilities. Some of the security features include encryption, IP masking, automatic WiFi security, SaaSPass and DNS filtering.
The VPN service provider has a number of comprehensive user management tools like Hybrid Secure Web Gateway. This helps you control user access and deal with malware before any damage is done.
3. Twingate — Best Free Remote Access Solution
- Fast speeds
- Free version
- Hardware-free & lightweight design
- Free version has limited features
Twingate is one of the most lightweight remote access solutions. Its stripped-down design gives it reliably fast connection speeds as it has minimal impact on the device you’re using in terms of RAM usage. Add its support for peer-to-peer connections, and you have a service that facilitates the rapid transfer of data no matter how far apart the connected users may be.
On top of its excellent speeds, Twingate is hardware-free, which reduces the need for constant maintenance. You can also rely on state-of-the-art security like encryption, DNS and content filtering, and zero trust security to keep unauthorized eyes out of your business. In addition, Twingate is one of the few alternatives on our list that offers a free version.
Conclusion
Small, medium and large organizations alike can use remote access VPNs to connect a large number of users to an office network remotely. Security features like encryption, DNS filtering and IP masking will ensure that sensitive data never falls into the wrong hands.
You can use Windows 10 or 11 to set up a single computer as a remote access VPN server. However, at the office level, it’s easier to use a dedicated service like NordLayer, Twingate or Perimeter 81.
Have you used a remote access VPN in the past? Based on your hands-on experience, how does the usability compare to a regular VPN? Tell us what you think in the comments below, and keep on reading our blog for more informative articles.
FAQ: Remote Access VPN Solutions
How to Implement a VPN for Remote Access?
You can implement a VPN for remote access by combining a VPN gateway, a VPN client and the right protocols with a user authentication framework that protects internal resources from unauthorized external access.Should I Use a VPN for Remote Access?
Yes, you should use a VPN to securely gain remote access to your organization’s private network. A remote access VPN encrypts all the data transmitted between your remote device and the network to prevent any form of interception from external parties.How to Access a Computer Remotely Using VPN?
You can remotely connect a computer to a secure network through a VPN gateway or server. You’ll need a verification mechanism that withholds access until after you authenticate your login credentials.What Is the Difference Between VPN and Remote Access VPN?
The main difference between a commercial VPN and a remote access VPN is that the former protects an individual on the wider public internet. On the other hand, a remote access VPN focuses on providing remote gateways and security to an organization’s private network.

Leave a Reply