What Is AES Encryption: The Algorithm Explained in 2025
Quick Summary: What Is AES Encryption?
AES encryption is one of the most secure ciphers. It encrypts different types of data to make it impossible for anyone without the decryption keys to access it. With current computers, cracking AES would take about a billion years.
If I had a dollar for every time I’ve mentioned AES encryption in the last three years, I would have a penthouse in Carre d’Or. It’s fundamental to the security of many cloud-based technologies, including the best VPNs. However, the truth is that not many people properly understand what AES encryption is and what it’s capable of.
Here’s the short of it: AES encryption is a highly secure cryptographic algorithm used to encrypt data with a single secret key. It is used to protect sensitive data across different applications for online communication, file storage and networks.
Today, I’ll be exploring the near-fantastic world of AES encryption. I will define it, explore its features and how it works, examine the types that exist and discuss the benefits. If you’ve always been curious about understanding AES encryption and all it entails, this article is for you.
What Is Advanced Encryption Standard (AES) Encryption?
Advanced Encryption Standard (AES) is a symmetric encryption algorithm that processes data in fixed blocks of 128 bits. To better understand it, we have to define each individual component.
The first is symmetric encryption. This is where a single key is used to encrypt and decrypt data. This means the sender and the receiver of an encrypted message must share the same key to access the message.
We also have bits, the most basic unit of information in computing (either a 1 or 0). With AES, there are two important bit measurements:
- The block size, which is always 128 bits (fixed).
- The key size, which can be 128, 192 or 256 bits.
The key length determines the level of security of the encryption. For example, a 128-bit key has 2128 possible combinations. AES supports three different key lengths: 128, 192 and 256 bits, with longer keys providing increased security.
The longer the length, the more secure the encryption — but don’t let that trick you into thinking AES-128 is a pushover. Despite being the smallest cipher, it has more than 3.4 quadrillion potential combinations.
To put that into perspective, if you started counting 3.4 quadrillion at the rate of one number per second, it would take you about 108 million years to finish. That’s roughly twice as long as it’s been since dinosaurs roamed the planet. This is why AES encryption is part of the bedrock of today’s online security.
AES History
AES traces its origins to January 1997, when the U.S. National Institute of Standards and Technology (NIST) held a contest asking the public to present alternatives to Data Encryption Standard (DES), which was quickly being overtaken by technological advancements.
NIST received 15 viable submissions from 12 countries. In October 2000, a cipher called Rijndael was accepted as the new Advanced Encryption Standard.
Breaking Down AES Encryption Features
AES uses symmetric encryption, large key sizes and open-source code to achieve the impenetrable digital security it’s known for.
- Symmetric key encryption: AES uses the same key to encrypt and decrypt data. This makes AES faster and easier to manage than asymmetric encryption. However, any encryption is vulnerable if the key is stolen, which is why VPN protocols use asymmetric ciphers to encrypt symmetric keys.
- Key sizes: AES encryption comes in three key sizes: 128, 192 and 256. The larger the key size, the stronger the encryption — though all are considered highly secure for most applications. However, larger key sizes require more computational resources and can be slower than smaller key sizes.
- Open-source: AES is open-source. The algorithm is freely available to the public and can be set up free of licensing charges. The open-source nature also permits security researchers to independently analyze the algorithm for vulnerabilities.
- Widely accepted standard: AES has high compatibility, which makes it the accepted standard for securing networks, web browsing, VPNs and more.
For more information on how AES and other symmetric algorithms work together with asymmetric encryption, see our full encryption guide.
Types of AES
AES encryption can be classed into three types based on the length of the cipher keys:
- AES-128: This uses a 128-bit encryption key for 10 rounds of encryption (that is, the encryption is applied to the text 10 times in sequence). AES-128 has more than 3.4 × 10^38 potential key combinations. As the fastest of the three, it provides data security for everyday applications like messaging services, WiFi networks and VPNs.
- AES-192: This type uses a 192-bit key, resulting in 12 rounds of encryption. This translates to about 6.2 × 10^57 possible key combinations, making it good for handling the secure transfer of very sensitive files.
- AES-256: This employs a 256-bit key with 14 rounds of encryption and more than 1.1 × 10^77 potential key combinations. AES-256 is so secure that the U.S. government uses it to protect all its classified communications and critical infrastructure systems.
How Does AES Encryption Work?
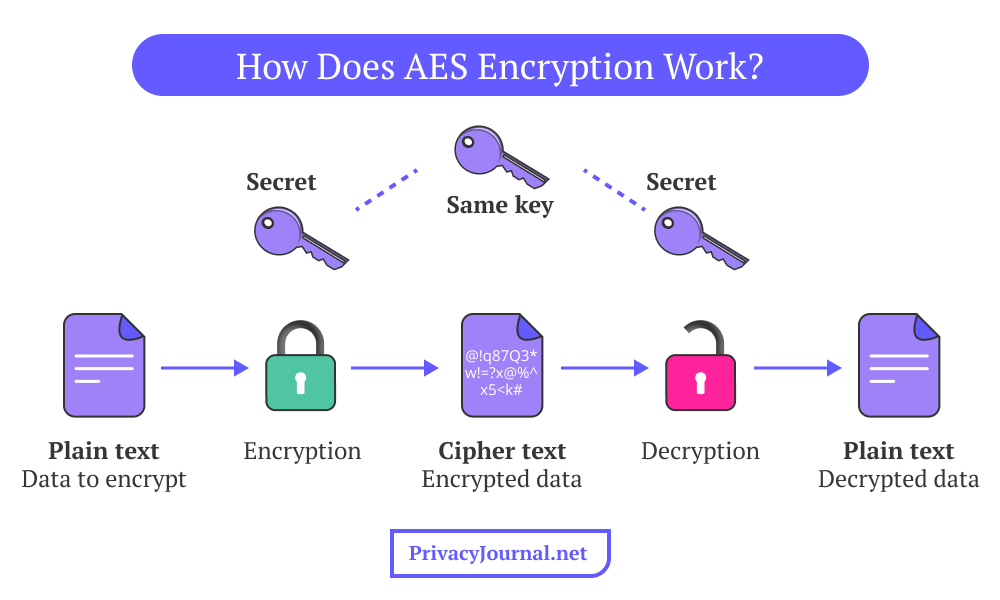
In short, AES encryption transforms plaintext into ciphertext and back by applying its keys to equal-sized data blocks. The full explanation of how AES encryption works is so intricate that I could pull a muscle just writing about it. I’ll simplify the process without the complicated jargon.
AES uses block ciphers, which means it divides plaintext into 128 blocks before encrypting it. The data within each block is divided into arrays of 4 by 4, or 16 bytes. Each of these 16 bytes contains a further 8 bits, bringing the entire number of bits per block to 128. Therefore, 128 bits of plaintext will produce 128 bits of ciphertext.
Each unit of encrypted data is replaced by a different unit based on the security key used. Since AES is a substitution-permutation cipher, it uses a key expansion process where the initial keys are used to come up with new keys for each round of modification, called round keys.
These round keys are generated over multiple rounds of modifications (10, 12 or 14 rounds, depending on the key size). There are four operations performed repeatedly in the following specific rounds:
- subBytes: This is a non-linear substitution step where each byte is replaced by a precomposed substitution box. The non-linearity provided by subBytes enhances security against attacks like linear cryptoanalysis (an attack that tries to break ciphers by finding linear connections between ciphertext, plaintext and key bits).
- ShiftRows: This is a transposition step where rows within the state matrix (a two-dimensional array that stores intermediate data during encryption) are shifted a specific number of positions to the left. The aim of this step is to introduce diffusion by mixing up byte positions and preventing attacks that exploit predictable patterns.
- MixColumns: In this step, each column in the state matrix is transformed with a multiplication operation to provide more data diffusion for better security.
- AddRoundKey: This is another key-mixing step where a block of data is combined with a round key to ensure the encryption is tied to your secret key. This makes it harder for attackers to break the encryption.
AES Decryption
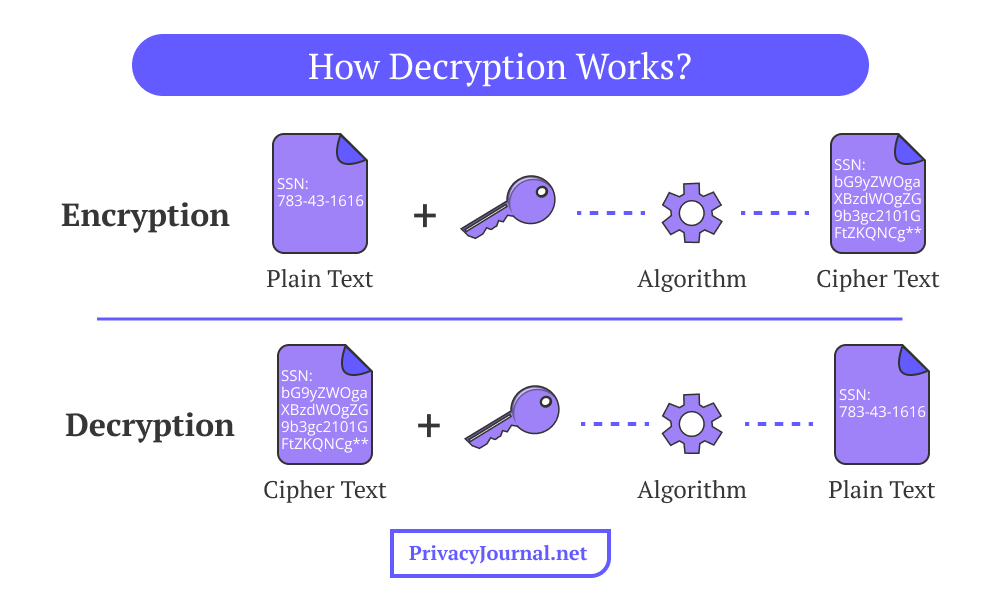
AES decryption is the process of converting scrambled ciphertext back into readable plaintext. Since it’s a symmetric cipher that uses the same keys for every step, the decryption process is simply the complete reversal of the encryption process I’ve described above.
The decryption process starts with the inverse round key, which is followed by the reversal of every encryption action — from byte substitution and row shifting to column mixing — until the original message is readable again.
How Is AES Encryption Used?
Owing to the high level of security it offers, AES encryption has a wide range of applications:
- VPN protection: Virtual private networks use AES and encryption like ChaCha20 to protect internet traffic for individuals and corporations. They encrypt regular internet traffic and pass it through a secure tunnel to prevent external parties from seeing where it originated or what’s being sent. The result is anonymity and privacy.
- Securing wireless networks: AES encryption is used for WiFi security protocols like WPA2 and WPA3. It encrypts all data transmitted over wireless networks to protect it from being hijacked.
- HTTPS browsing: Modern websites use AES encryption as part of the HTTPS protocol that secures data transmission between servers and browsers. This shows how symmetric and asymmetric encryption work together — symmetric encryption secures data transfer, while asymmetric encryption secures key exchanges.
- Mobile applications: Banking, messaging and social media apps that handle personal data usually use AES encryption to protect users from hackers. Signal, WhatsApp and Telegram are examples of messaging apps that use AES for end-to-end encryption.
- Government and military communications: AES encryption is so secure that nations use it to protect crucial communication between government agencies and military operations.
Benefits of AES
AES encryption has a long list of benefits:
- Easy to use: Though the processes behind AES are complicated, actually using it is easy. AES encryption comes ready to use out of the box for common applications like VPNs and messaging apps, so you don’t need to configure anything from scratch.
- Free: AES encryption is open-source, so developers don’t need to pay any license fees to use it.
- Versatility: AES can be used across a wide range of applications. You can encrypt hard drives, databases, internet traffic, IoT devices, VPNs and more.
Attacks on AES Encryption
While AES remains one of the most secure encryption standards, no security system is completely invulnerable. Although most of these are academic or theoretical, some known attack vectors include:
- Related-key attack: This attack occurs when an attacker observes the results of encryption with several different keys, then uses their mathematical relationships to deduce the value of the keys. Theoretical attacks have been demonstrated against AES-256 in academic settings, but they remain impractical in real-world conditions.
- Side-channel attack: This attack doesn’t focus on the algorithm itself, but its implementation. It exploits information leaked during the AES computation process. Timing variations, power consumption and electromagnetic emissions can be leaked and studied by a hacker, who can deduce what the system is doing without actually cracking the code.
- Known-key distinguishing attack: In this attack, a hacker tries to breach AES encryption using a known key.
- Key-recovery attacks: This aims to recover the encryption key through various techniques. Of all the proposed theoretical approaches, none have proven practical against properly implemented full-round AES, working only against reduced-round versions or weakened implementations.
How Secure Is the AES Encryption Algorithm?
AES encryption can’t be cracked with brute-force attacks. Even with incredibly powerful hardware, it would take approximately one billion years for a brute-force attack to crack the simplest AES type, AES-128. For comparison, a DES key, which I cover in the next section, can be cracked by modern computers within minutes.
However, that could all change if and when quantum computing comes into play, which is why some virtual private networks are already implementing post-quantum encryption.
Fully implemented AES encryption has never been cracked, as far as we know, and most experts agree that it will continue to be a reliable security option for decades to come. Even the U.S. government has complete confidence in using AES encryption.
AES vs DES
DES (Data Encryption Standard) is an encryption algorithm developed in 1977 that the U.S. government used before replacing it with AES. DES divides any given data into two parts and then works on each part separately using expansion, permutation and substitution.
Expansion is where the input is expanded to a larger size after the duplication or addition of bits in an encryption process. Permutation entails arranging the order of bits based on a fixed rule to contribute to diffusion. Substitution involves replacing bits with other bits through predefined mapping to introduce non-linearity.
DES is no longer widely used because it is less secure. It has a shorter key length of just 56 bits, compared to AES’ minimum of 128 bits. With current processing power, brute-force attacks can crack DES within minutes. Still, it is one of the algorithms that laid the foundation for developing AES.
AES vs RSA
RSA (Rivest-Shamir-Adleman) is an encryption algorithm also developed in 1977 that’s still considered secure. It uses public and private keys to encrypt and decrypt data; the public key is disclosed but the private key remains hidden. The use of different keys makes it an asymmetrical encryption algorithm, unlike AES, which is a symmetric encryption algorithm.
However, compared to the AES algorithm, RSA is slower, especially when dealing with large datasets. Furthermore, the keys used have to be considerably large (up to 4096 bits) for better security, which causes performance issues. That’s why RSA is often used simply to encrypt AES keys, with AES being used for the message itself.
Here’s a comparison table for the three encryption algorithms:
| ATTRIBUTE: | AES | DES | RSA |
|---|---|---|---|
| Type | Symmetric | Symmetric | Asymmetric |
| Key Lengths | 128, 192, 256 bits | 56 bits | 1,024, 2,048, 4,096 bits |
| Speed & Efficiency | Fast & efficient | Slower than AES | Slower than AES & DES |
| Encryption Process | Substitution-permutation network | Feistel network | Modular exponentiation network |
| Attack Resistance | Highly secure against brute-force attacks, vulnerable to quantum attacks | Vulnerable to brute-force attacks | Vulnerable to quantum attacks |
| Key Management | Easy, as it uses only one key | Easiest, as the keys are the shortest | More complex, as it separates keys into public and private |
Conclusion: Advanced Encryption Standard (AES)
That’s the black and white of the AES encryption algorithm. It has been the go-to security option for people and institutions, including governments, for more than two decades. Considering that it has never been fully breached, experts agree that it will continue being the preferred choice for the foreseeable future.
The biggest concern regarding AES encryption lies in the potential threat of quantum computing. With bigger and faster processors rapidly being developed, AES could be rendered obsolete sooner than expected. However, AES-256 has stood up to quantum attacks so far, so we might still be using it years from now. It’s hard to know for sure.
Have you used any applications that rely on AES encryption? How about virtual private networks? Are you confused by anything, from symmetric block cipher algorithm to secure data exchange? Tell us what you think in the comments below and we will be happy to engage with you. Keep reading our blog for more educational posts like this one.
FAQ: AES Online Encryption
What Is AES Encryption?
AES encryption is a symmetrical encryption that converts plaintext into ciphertext using keys that make it indecipherable to anyone who doesn’t have the decryption key.Is AES the Strongest Encryption?
At the moment, AES is one of the strongest symmetric encryption ciphers. It secures data using multiple rounds of keys, making it extremely hard to crack using even the best computers that modern technology has to offer.Is AES Still Recommended?
Yes, AES encryption is still recommended, as it has never been cracked. Experts have confidence that it has even more to offer for the coming decades.Is AES Still Considered Secure?
Yes. AES is considered secure, as it hasn’t been cracked since being developed and outperforms alternatives like DES.

Leave a Reply