
What Is IKEv2: The Internet Key Exchange Protocol Explained in 2026
Quick Summary: What Is IKEv2?
IKEv2 is a closed-source tunneling protocol available on many VPN services. It encrypts your online traffic alongside IPsec, resulting in a fast VPN connection that is stable enough to switch networks without interruptions.
If you have used some of the top VPNs, like ExpressVPN and Surfshark, you’ve probably encountered the IKEv2 (Internet Key Exchange version 2) protocol. This protocol is known for its good speeds and security, but that doesn’t quite answer the question: “What is IKEv2?”
IKEv2 is a widely accepted standard of cryptographic security. It’s especially good at maintaining connection stability, making it ideal for mobile devices that switch between mobile data and WiFi as they move. However, there’s more to IKEv2 than that. Gaining access to IKEv2 is now one of the most common benefits of VPN protection.
This article explores everything you need to know about the IKEv2 protocol, including how it works, what ports it uses, its pros and cons, and a detailed guide on how to set it up. Read on to find out more information.
What Is a VPN Protocol?
A VPN protocol is a set of instructions that a virtual private network (VPN) server uses to communicate with other devices on your behalf while maintaining encryption. When you connect to a VPN server, the VPN protocol determines the type and level of VPN encryption that secures your data from interception.
VPN protocols also dictate the authentication method that confirms the identity of the devices at either end of the encrypted tunnel. You can read more in our “VPN protocols” article.
What Is IKEv2? Meaning Explained
IKEv2 is an acronym for “Internet Key Exchange version 2.” It’s a tunneling protocol built on the Oakley Key Determination Protocol and ISAKMP. The protocol was introduced in 1998 as IKE before it was updated to IKEv2 in 2005.
The major improvements that were implemented in 2005 included reducing the number of message transmissions in the main mode from six to four, which made IKEv2 faster. Additionally, IKEv2 saw the addition of modern encryption ciphers like AES, so it’s more secure than its predecessor.
Over the course of the 2010s, IKEv2 was widely adopted as one of the standard protocols for virtual private networks. It’s been available for some time on my favorite service, ExpressVPN, as you can read in our ExpressVPN review.
How Does IKEv2 Work?
When using a VPN, IKEv2 authenticates the link between your device and the VPN server, and dictates the type of security to be used. This process is called a security association, and it generates the same encryption keys that are used to encrypt and decrypt the data transferred through the secure tunnel.
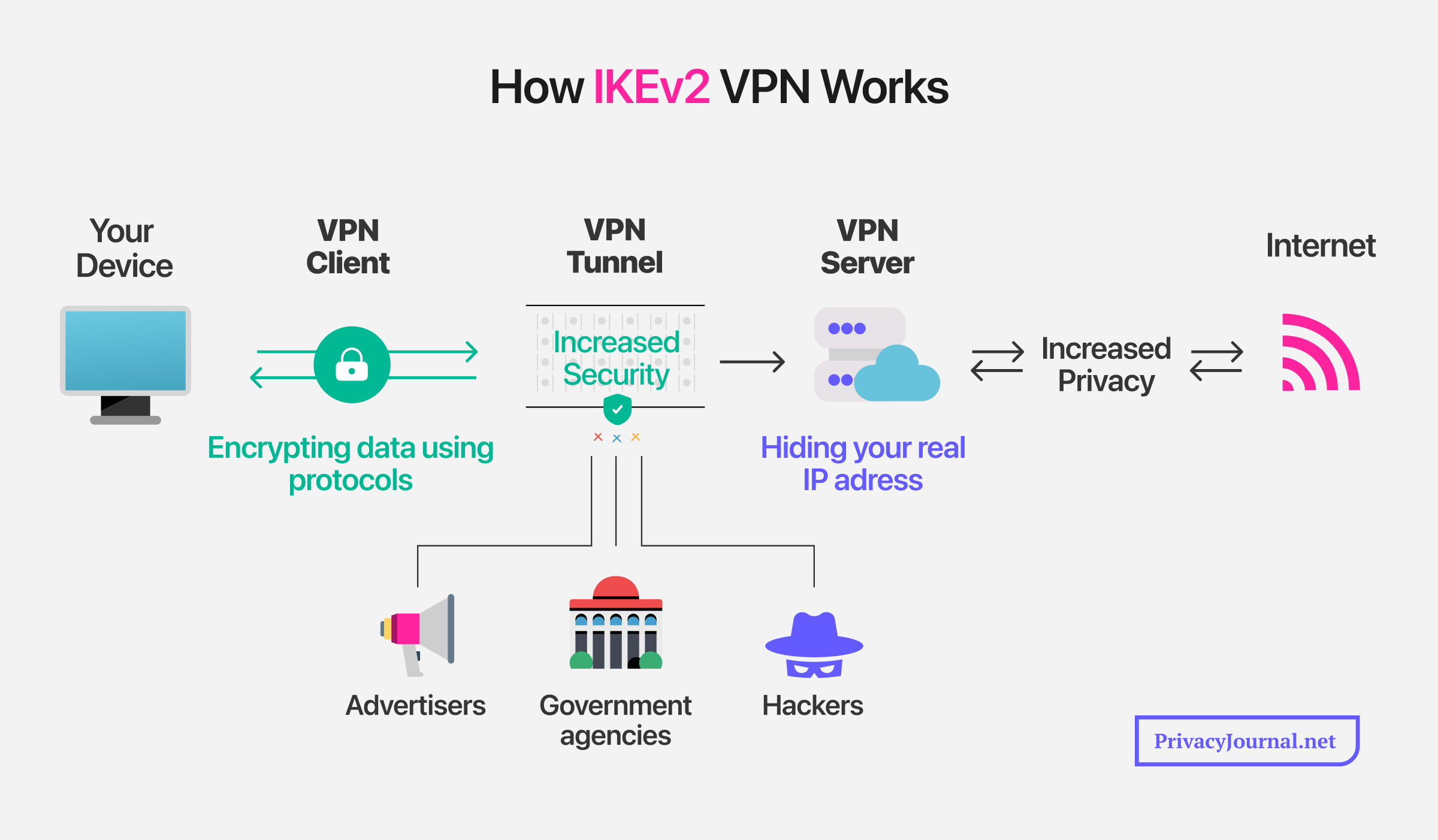
Is an IKEv2 VPN Safe to Use?
IKEv2 is a highly secure VPN protocol that uses the Diffie-Hellman key exchange algorithm. This works by agreeing to and calculating secret arithmetic keys between parties connected through an insecure channel. These keys prevent anyone else from intercepting this connection.
Additionally, IKEv2 uses end-to-end encryption ciphers, including Blowfish, AES and Camellia. Blowfish utilizes a single key to encrypt and decrypt data, and that simplistic setup makes it one of the fastest ciphers employed by IKEv2.
On the other hand, AES uses a key expansion process in which an initial encryption key is used to generate new keys called round keys. In total, AES-256 generates 14 rounds of these keys, creating a functionally uncrackable cipher that helps make VPNs safe.
The last cipher, Camellia, uses secret key sizes of 128, 192 and 256 bits. It’s as secure and fast as AES-256, but it’s not widely used because it’s a newer cryptographic cipher.
Why Is IKEv2 Always Paired With IPsec?
IKEv2 is always paired with the IPsec protocol suite, creating a complete protocol that provides the best speeds possible without affecting the level of security. Microsoft and Cisco collaborated to make this possible.
While IKEv2 is efficient at managing security associations, IPsec excels at payload encryption. IKEv2 negotiates the security attributes that IPsec will use, while IPsec handles the quick encryption and decryption of the actual data. This collaboration makes for fast reconnection after a network disruption — perfect for switching from a mobile network to WiFi.
IKEv2 Ports
The default port that IKEv2 uses is UDP 500. It’s less susceptible to latency drops or spikes, giving it the stability needed for smooth performance. Other available ports include ESP IP Protocol 50 — which isn’t based on TCP or UDP protocols — and this causes connection issues for NAT devices.
To solve these connection problems, IKEv2 relies on Port 4500, which allows ESP sessions to be encapsulated within a NAT-friendly UDP packet.
Advantages & Disadvantages of Using IKEv2
Like all security protocols, IKEv2 has strengths and weaknesses. As we explore them, it’s also a good idea to be aware of the reasons why you should use a VPN in the first place.
IKEv2 Advantages
These are the advantages of using IKEv2:
- Speed: The combination of IKEv2 and IPsec streamlines the encryption process, allowing data to transfer much faster than other protocols like OpenVPN TCP. This also makes it a resource-friendly protocol that’s easy on data and battery life, which is ideal for smartphones.
- Stable connections: The mobility and multi-homing protocol for IKEv2 (MOBIKE) feature allows you to switch smoothly between networks without causing disruptions. This is another reason why IKEv2 is better if you frequently switch between mobile and WiFi networks.
- Secure encryption: IKEv2 combines AES-256, Blowfish and Camellia ciphers that are almost impossible to break. You can even connect to unsecured public hotspots without worrying about being hacked.
- Compatibility: IKEv2 can be implemented on a wide range of devices. These include smartphones, tablets, computers, smart TVs, routers and any device that supports VPNs with the IKEv2 protocol.
IKEv2 Disadvantages
These are the disadvantages of using IKEv2:
- Easily blocked: IKEv2 uses UDP port 500, which isn’t part of the standard ports that are used by web servers. Network administrators can easily block UDP port 500, rendering IKEv2 unusable.
- Additional configurations: While IKEv2 works on many devices that have native support for the protocol, you’ll need to manually configure it on platforms that lack it. The process isn’t hard, but it can still be complicated for inexperienced users.
- Closed-source: IKEv2 is a closed-source tunneling protocol. This doesn’t mean it’s unreliable or vulnerable, but there’s no way to tell if it has backdoors — it’s not possible to inspect it, unlike with open-source protocols such as OpenVPN and WireGuard.
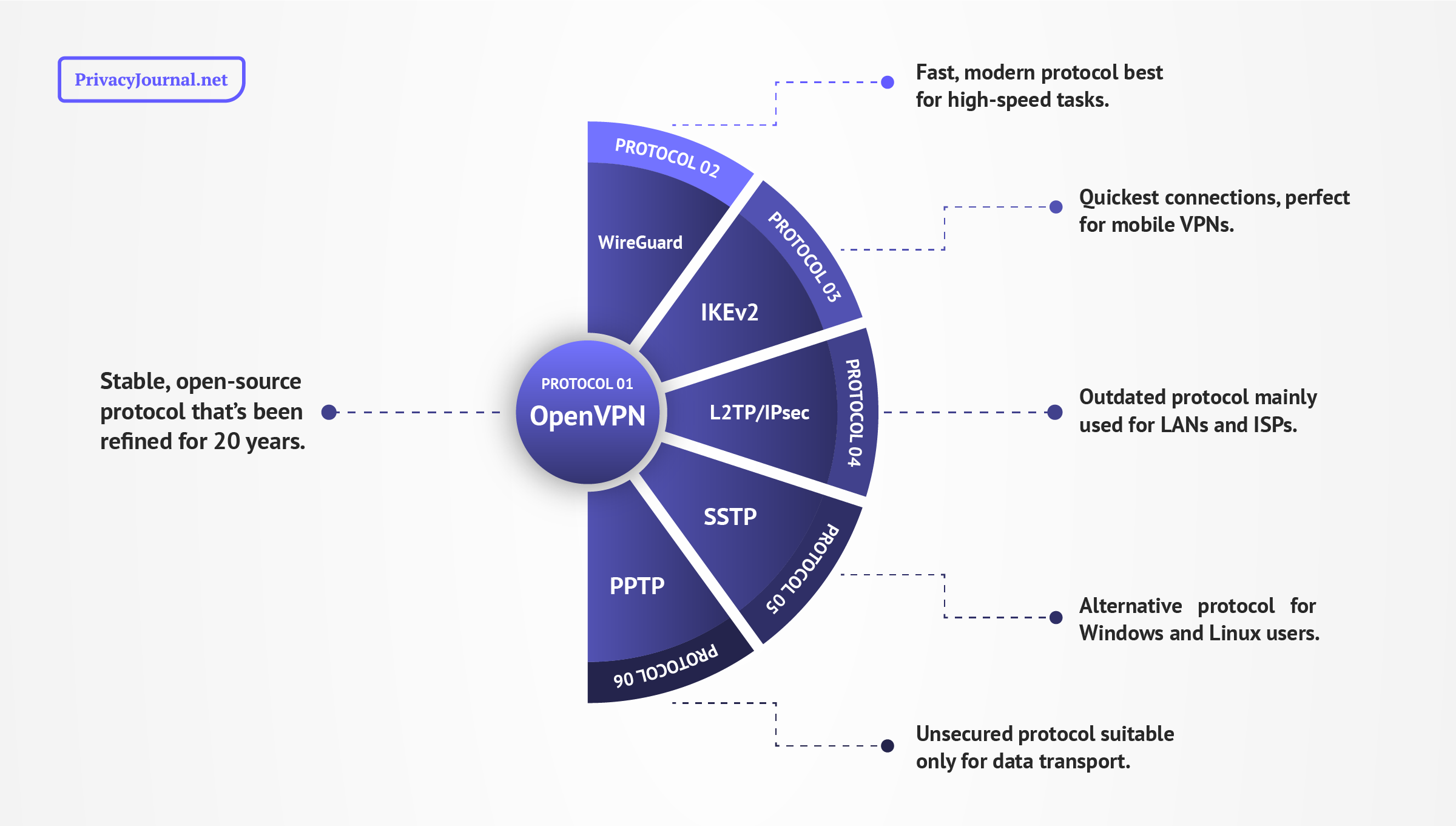
IKEv2/IPsec Compared to Other VPN Protocols
| Protocol | Speed | Security | Encryption | Native OS |
|---|---|---|---|---|
| OpenVPN | Fast (TCP) Not very fast (UDP) | Uncrackable | Entire OpenSSL library* | N/A |
| WireGuard | Very fast | Uncrackable | ChaCha20 | N/A |
| IKEv2 | Very fast | Secure | Several types via IPsec | N/A |
| L2TP/IPsec | Fast | Secure | Several types via IPsec | N/A |
| SSTP | Very fast | Uncrackable | AES-256 | Windows |
| PPTP | Very fast | Not secure | MPPE | N/A |
IKEv1 vs IKEv2
IKEv2 is an improved version of IKEv1. Firstly, IKEv2 supports more encryption algorithms, including modern asymmetric authentications. Secondly, IKEv2 offers stable connections via MOBIKE, using less bandwidth than IKEv1. IKEv2 is also faster than IKEv1 as it natively supports Network Address Translation-Traversal (NAT-T), which speeds up connections.
IKEv2 vs WireGuard
IKEv2 and WireGuard have many similarities. Both protocols use UDP ports, which can be blocked by firewalls. Additionally, they offer amazing speeds that are ideal for streaming or torrenting. However, WireGuard is open-source, making it more transparent than IKEv2 — although it’s still a newer protocol that hasn’t been scrutinized as much as IKEv2.
IKEv2 vs OpenVPN
You get the same level of protection from IKEv2 and OpenVPN, which both use AES-256 encryption. IKEv2 offers better speeds than OpenVPN, but you’re less likely to be blocked by firewalls on OpenVPN as it uses ports 443 and 1194. OpenVPN is also the only transparent open-source option between these two.
IKEv2 vs L2TP/IPsec
IKEv2 and L2TP/IPsec provide the same level of security since they both work around IPsec. However, IKEv2 offers better speeds than L2TP/IPsec, which encapsulates data twice while transferring it through the tunnel. On the other hand, L2TP/IPsec has wider native system support than IKEv2.
How to Set Up IKEv2 on Your VPN
IKEv2 is supported by VPNs like ExpressVPN, NordVPN and Surfshark. However, its actual availability depends on the operating system you’re using. For most devices, it’s available on iOS and macOS, and you can set it up where available using the following general steps.
1. Subscribe to a VPN of your choice that offers an IKEv2 protocol.
2. Download and install the VPN on a supported device.
3. Open the app settings and find the “protocol” tab or drop-down list. Select IKEv2 from the options. You’re now ready to use the internet with an active IKEv2 connection.
You can also set up IKEv2 manually on Windows, iOS, Android, macOS and Linux. The process involves generating VPN certificates and authentication information, which many VPN services let you download with a paid account. You’ll have to import the IKEv2 VPN configuration to your desired device, then manually configure it throughits network controls.
Conclusion
IKEv2 is a fast and secure VPN protocol that keeps you safe and works well on mobile devices. Thanks to the optimization produced by combining it with IPsec, it doesn’t consume too much data or battery life. While it has a few drawbacks, like vulnerability to firewall blocks, IKEv2 is a protocol that I never hesitate to switch to when I need fast speeds.
Have you ever used IKEv2 before on any of your devices? How fast was it compared to WireGuard and other fast protocols? Have you ever experienced firewall blocks on any network when using IKEv2? Tell us your thoughts in the comments below, and keep reading our blog for more amazing posts.
FAQ: IKEv2 VPN Protocol
What Does an IKEv2 VPN Do?
An IKEv2 VPN encrypts your internet traffic using ciphers like AES-256, which makes it harder for anyone to intercept your traffic and snoop on your activities.Is IKEv2 Vulnerable?
IKEv2 is vulnerable to firewall blocks as it uses UDP port 500. This port can be blocked easily by network administrators, which would make the protocol unusable.Should I Use IKEv2 or OpenVPN?
Depending on your needs, you can use IKEv2 or OpenVPN. IKEv2 is good for fast speeds and stable connections, but you can switch to OpenVPN if you encounter firewall blocks.Which Operating System Supports IKEv2 VPN Client for Azure Point-to-Site VPN?
The IKEv2 VPN client for Azure Point-to-Site VPN is supported on Windows, macOS and Linux.

Leave a Reply