What Is a VPN Tunnel? Explanation of How It Works for 2025
Quick Answer: How Does VPN Tunneling Work?
A VPN tunnel encrypts your internet traffic data as it travels between your device and the VPN server, letting you use the VPN server as a proxy without revealing your real identity.
What is a VPN tunnel? If you’re picturing a hole in the ground, you’re not alone. Virtual private network (VPN) companies talk a lot about tunneling, but their technical explanations of the concept leave plenty of gaps — even the best VPNs stumble here. I thought I’d take a shot at writing the explanation I wish I’d had when I started out with VPNs.
In simple terms, a VPN tunnel is the link between your device and a VPN server. All information is encrypted before it leaves your computer or phone, and it is decrypted only when it reaches the VPN location. Imagine it like your internet connection entering a tunnel near your home router and not emerging until it reaches the VPN server.
In the rest of the article, I’ll explain how VPN tunnels work, what they do to keep you safe and how you can use one.
Last updates:
- 05/21/2024
Updated to add custom graphics
What Is a VPN Tunnel? The Basics Explained
Here’s how the internet works when you aren’t connected to a VPN:
- When you type a URL into a browser, the router sends a request to see the corresponding web page.
- Your internet service provider (ISP) relays the request to a domain name system (DNS) server, which looks up the server where the URL can be found.
- The server then sends the information back to you.
The problem is that all this activity is totally exposed. Your unique IP address allows your ISP and the DNS to see exactly who you are and which websites you’re looking at. A VPN tunnel solves this problem by encrypting every outgoing message from your device, sending it to a server in its own network and then decrypting it before moving it along to your ISP.
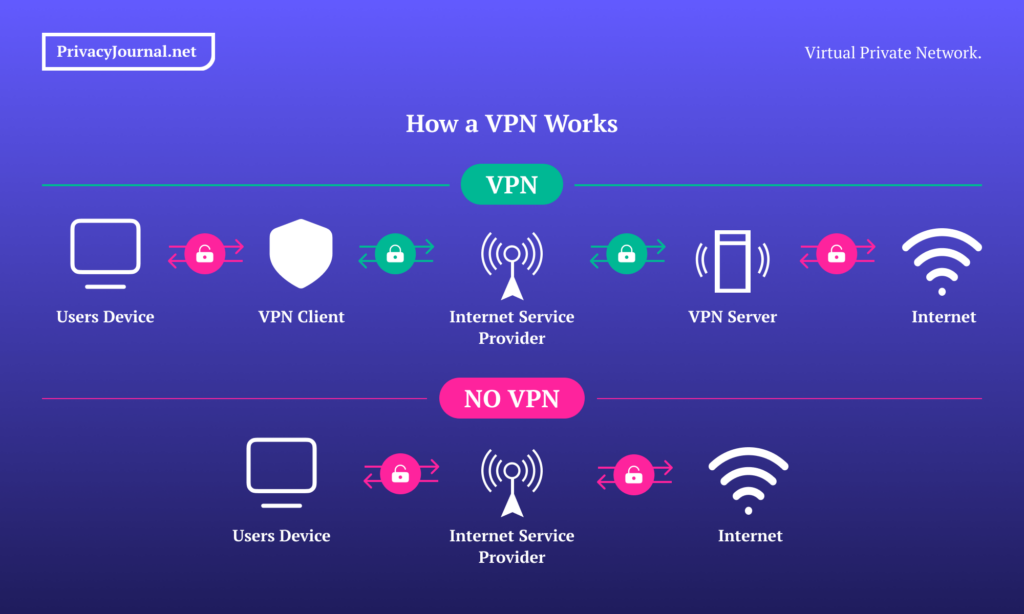
The end result is that ISPs can see what you are doing online but cannot connect your identity to that activity. It’s as though you hire someone to go to the store for you and they conceal the purchase until they get back to your house. You use the internet through a proxy, which keeps all your secrets safe with an encrypted connection.
How Do VPN Tunnels Work?
This part is a bit technical, but I’ll try to avoid jargon. When a website transmits from a server (where the website is hosted) to a client (the machine you use to look at the website), the data doesn’t move all at once. Instead, it’s broken into packets and reassembled at its destination. This makes the process smoother, like taking furniture apart to fit it through a doorway.
A VPN moves data packets the same way, but it encapsulates each packet inside another packet. This outer packet is generated with an encryption protocol — a set of rules for encrypting and decrypting data packets at each end of the tunnel. Thanks to the protocol, packets can reach their destinations even if your ISP can’t read them.
Don’t worry if you don’t fully understand this right away. A VPN service will take care of it all for you. You can also read my VPN guide that explains more information about why you need a VPN connection.
To keep your data safe in a VPN tunnel, you just need to follow these steps:
- Subscribe to a VPN service. I recommend NordVPN; see my NordVPN review to learn why.
- Download and open a VPN client. Be careful, as not every VPN supports every device and browser. Nor do all VPNs support all operating systems.
- Choose a VPN server and connect. Pick a nearby server location for the best speeds, or choose one in a different country to access that region’s geo-blocked sites.
- Use the internet as normal. Until you disconnect from the VPN, you’ll be able to use the internet with the VPN server acting as your server.
VPN Split Tunneling Explained
You may also have heard of VPN split tunneling, which can be a useful feature — though it’s another slightly misleading term. By default, an active VPN sends all the data from your computer through an encrypted tunnel. With split tunneling, you choose which types of traffic get encrypted and which do not.
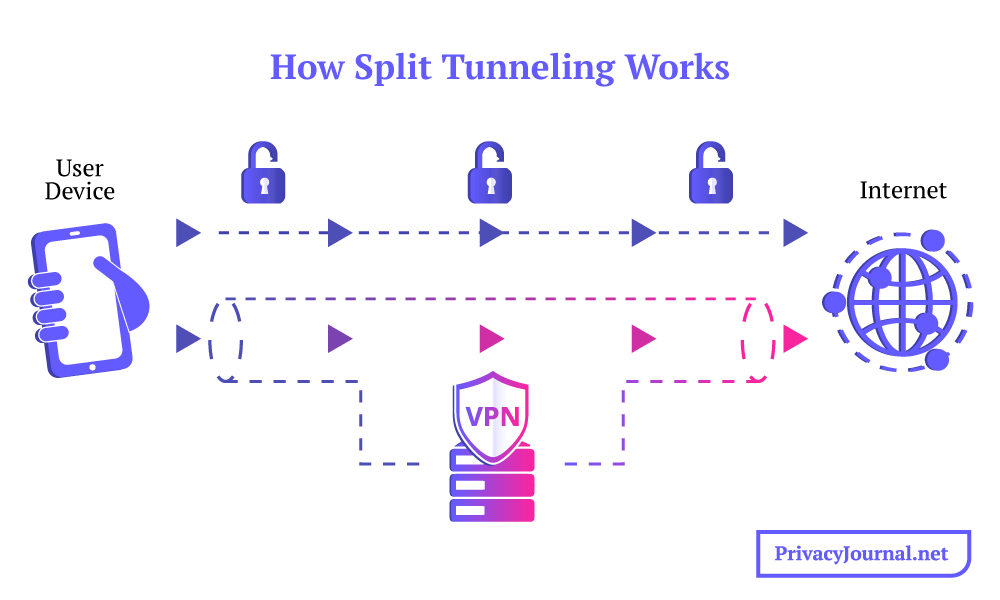
Split tunneling works by separating data into encrypted and unencrypted packets.
As useful as VPNs are, they can sometimes cause trouble. Some sites automatically block VPN traffic, and congested servers can occasionally make your internet lag. Split tunneling means you can keep your most sensitive information encrypted while simultaneously going without encryption for the few tasks that a VPN would just get in the way of.
Torrenting is one of the most common use cases for VPN split tunneling. You can set a torrenting client to run in the background with VPN protection so your ISP doesn’t catch you and throttle your speeds. While you wait for your download, you can take care of quick online errands that won’t lead to potential legal trouble. Read our best VPN for torrenting guide for more information.
How Secure Is a VPN Tunnel?
As long as you’re using a good service and a reputable protocol (see the next section), your VPN tunnel will be secure against 99% of attacks. There’s no such thing as impenetrable security, but your encryption doesn’t have to be completely unbreakable to protect against all the threats you may encounter online. The eventualities I list below are exceedingly unlikely.
As you’ll see next, the PPTP, L2TP and SSTP protocols are not perfectly secure, so a tunnel using any of these might be hackable. Any tunnel using an obsolete encryption algorithm like SHA-1 or Blowfish is also vulnerable. Additionally, a VPN can leak for reasons other than the tunnel itself — for example, due to WebRTC leaks or because it uses a third-party DNS.
It’s also possible for a VPN to leak information if hackers capture one of its servers, which happened with NordVPN in 2018. You can read more about this in my NordVPN review. Finally, if hackers steal the encryption key of a VPN that doesn’t use perfect forward secrecy (the practice of regularly changing encryption keys), they may be able to compromise the tunnel.
The Different Types of VPN Tunneling Protocols
Let’s go over this once more. VPN tunnel protocols wrap every data packet in another packet, which encrypts the data until it reaches its destination — the VPN server — at which point it can be decrypted. The VPN protocol governs this process, which is a set of instructions to ensure each packet reaches its destination while remaining encrypted over a secure connection.
In this section, I’ll rank the six most common VPN protocols in order of security, with the first one being the strongest. I’ll only list widely used protocols, but I’ll mention proprietary options as they become relevant.
1. OpenVPN
OpenVPN is the most secure VPN tunneling protocol not just because it’s an open-source protocol — WireGuard is, too — but because it’s been open-source for longer than any other. Volunteers from the security community regularly comb through its code to look for vulnerabilities and potential updates. Since no one owns it, no one has any incentive to conceal its flaws.
For privacy nerds like me, OpenVPN will remain the gold standard until WireGuard has another eight or so years under its belt. It uses AES-GCM-256 encryption by default, but it also works with ChaCha20, the other top cipher currently available.
2. WireGuard
WireGuard has recently staked its claim as OpenVPN’s successor. With a much smaller codebase, it’s theoretically less vulnerable. Like OpenVPN, WireGuard is open-source, but there’s a lot less code to comb through in search of flaws. However, since time is the only real guarantee of security, I’ve ranked WireGuard lower because it’s newer.
The one known problem at the moment is that WireGuard’s speed comes in part from omitting some of OpenVPN’s security checks. It stores your personal IP address on the server unless the VPN service takes specific precautions to prevent this — and you can bet not all of them do. I recommend being careful with WireGuard unless you’re using a vetted VPN service.
3. IKEv2
IKEv2 (Internet Key Exchange version 2) is often faster than OpenVPN and WireGuard, and uses equally strong security, employing the Internet Protocol Security (IPsec) suite with AES-256 encryption.
It’s the fastest protocol for picking up dropped connections when moving between networks. Experts trust IPsec, and IKEv2 is almost always as safe as WireGuard and OpenVPN. It’s a good choice for VPNs on mobile devices.
It comes in third place for two reasons. First, it’s not open-source; Cisco and Microsoft jointly own its code. Vulnerabilities take longer to find without a robust volunteer community. Second, IPsec only works with UDP port 500, a known VPN vector that is easier to block. I don’t advise using IKEv2 in any country with restricted internet, especially China.
4. SSTP
SSTP (Secure Socket Tunneling Protocol) is very safe, since it uses AES-256 by default. Like OpenVPN, it uses UDP port 443, as do most websites on the HTTPS standard. This makes it much harder to block than IKEv2. However, it has the same basic problem as IKEv2: Microsoft owns its source code.
Lest you think I’m being paranoid, remember that Microsoft collaborated with the NSA PRISM program, installing backdoors in many of its apps through which the government could harvest data without search warrants.
5. L2TP/IPsec
L2TP (Layer 2 Tunneling Protocol) is an older protocol that’s mostly been phased out. It has no native encryption, so it’s only safe when paired with IPsec. Unlike IKEv2, which only uses IPsec to authenticate secure connections, L2TP relies on IPsec for all its security. With the top three protocols being both faster and safer, there’s no good reason to use L2TP anymore.
6. PPTP
PPTP (Point-to-Point Tunneling Protocol) is the only genuinely unsafe protocol on this list — if you see a VPN offering it, do not use that VPN. It uses outdated security for both authentication and encryption, as it relies on the RC4 cipher, which several known methods can crack.
Conclusion
By now, I hope I’ve helped you understand what VPN providers are talking about when they advertise secure VPN tunnels. The tunnel is simply a useful metaphor for encryption and decryption — the reality looks more like locking your data in several secure boxes and loading them onto a truck.
Now that you know what a VPN tunnel is, you should be well equipped to choose the right VPN provider. Which one did you settle on? Which tunneling protocols work best for you? Do you have any other questions about security technology? I’d love to hear them in the comments. Thanks for reading!
FAQ: VPN Tunneling
What Does a VPN Tunnel Do? How Does VPN Tunneling Work?
A VPN tunnel encrypts your online activity so your internet traffic can’t be traced back to you. This protects you from invasive ads, hackers, government surveillance and more.How Do I Get a VPN Tunnel?
You can use a VPN tunnel by subscribing to a VPN service, downloading a client app and connecting to any server. You can also set one up manually, but it’s more complicated.What’s the Best VPN Tunnel Protocol?
OpenVPN is the most secure protocol, is compatible with the latest algorithms and is constantly vetted by a volunteer community. WireGuard is a close second but needs to be tested over a longer period of time.

Leave a Reply