
What Is Split Tunneling for VPN Services? 2025 Guide
Quick Summary: What Is Split Tunneling?
Split tunneling is a feature that lets you control how VPNs route your internet traffic. There are three types of VPN split tunneling: URL-based (you choose which websites open via the VPN), app-based (you funnel some apps through the VPN) and inverse split tunneling (when you specify apps or URLs that don’t go through the VPN tunnel). Note: not all VPN apps offers split tunneling on all operating systems.
NordVPN, the best split tunneling VPN, offers this feature on Windows, Android and Android TV. The VPN service comes with a risk-free 30-day money-back guarantee.
Split tunneling is a networking configuration available on many of the best VPNs that allows you to control how your internet traffic is routed. It splits your internet traffic into secured traffic, which passes through a VPN server, and unsecured traffic, which goes through your normal internet connection.
Using split tunneling can reduce the average processing time on your browser. It also lets you manage how you protect your internet traffic. This article will explore everything there is to know about split tunneling, including how to enable it, its benefits and drawbacks, and what VPN services offer it.
- Money-Back Guarantee30 DaysWorldwide Server AmountOver 5,400+ servers in 59 countries
What Is VPN Split Tunneling?
Split tunneling is a VPN feature that lets you route some of your internet traffic through a secure connection while leaving the rest unprotected. The selective routing of traffic optimizes internet usage by ensuring that only necessary requests go through the VPN speed bottleneck.
VPN encryption usually takes a toll on your internet speed as your data gets routed through extra steps outside the regular path that your internet service provider (ISP) uses. You may experience higher latencies when connecting to VPN servers that are farther from your physical location.
Split tunneling is commonly found on the best VPNs for torrenting. An encrypted VPN tunnel can protect torrent clients from copyright trolls in the background while you get your full internet speed for all other tasks.
How Does VPN Split Tunneling Work
Split tunneling works by dividing your traffic into secured and unsecured paths. To better understand it, you must first grasp the basics of how internet connections and VPN servers work.
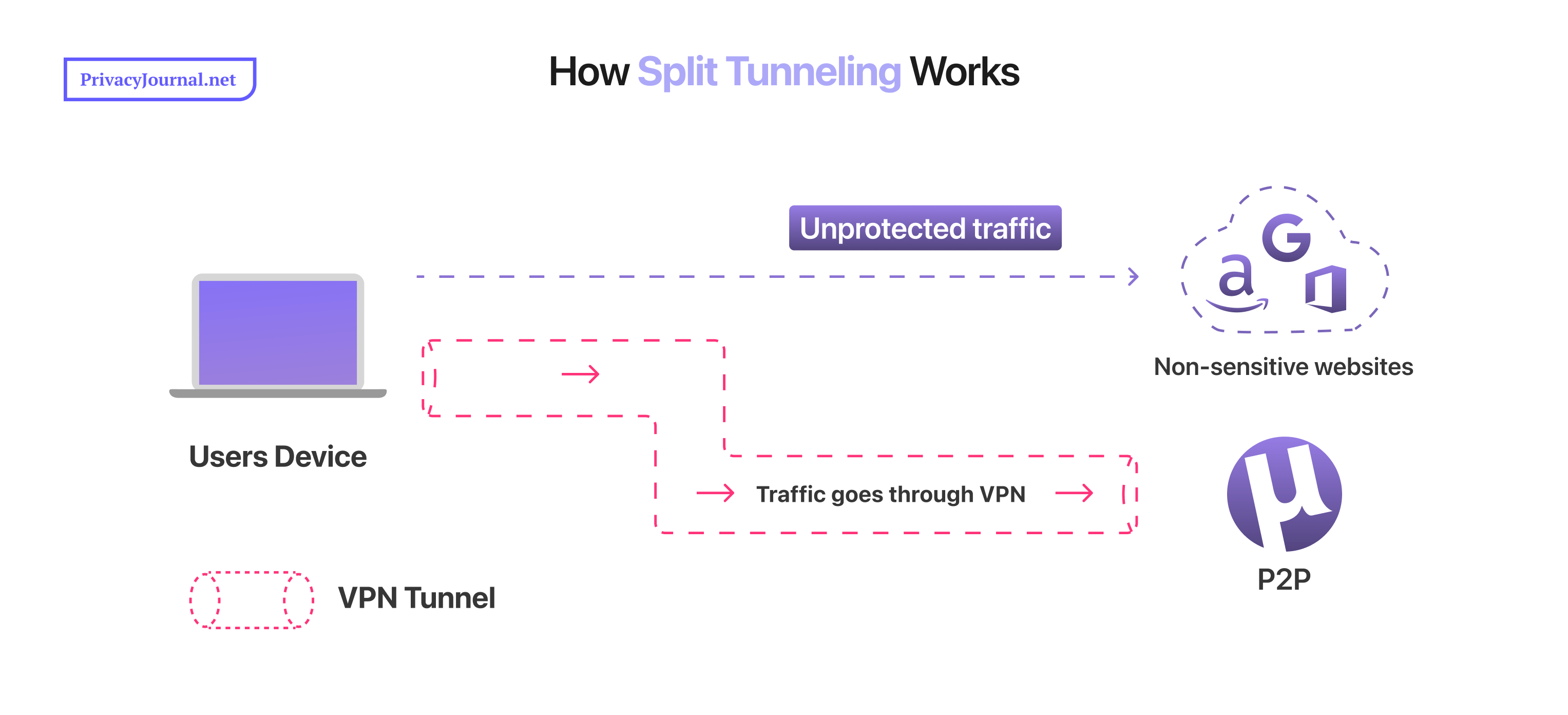
Ordinarily, whenever you send a request to view a website, your device communicates with your internet service provider. Your ISP then routes this request to the target website and back to your device. It’s pretty straightforward.
When you add a VPN to this equation, an additional secure path is established. The VPN becomes an intermediary between your device and the final destination of your requests. It routes these requests through its own servers and encrypts its communications with your device to hide your browsing data from everyone, including your ISP.
However, introducing a VPN’s secure path sometimes comes at the expense of connection speeds, and that’s where split tunneling comes in. Split tunneling encrypts only the parts of your traffic that you decide to protect. This reduced encryption load can bump up your connection speeds.
Split Tunnel vs Full Tunnel
“Full tunnel” means using the default VPN configuration that encrypts all your internet traffic. It fully protects all data sent and received on your device. “Split tunnel” involves dividing your internet traffic into two paths. Part of the traffic is routed through the VPN for full protection, while the rest is sent over the normal unsecured network.
Types of VPN Split Tunneling
There are three types of split tunneling that virtual private network services use today. Some of these may be combined within a single service.
- URL-based split tunneling: Split tunneling by URL lets you choose which websites will open through the VPN and which will open over your regular internet connection. The NordVPN extension for Chrome is an example of a service that offers URL-based split tunneling.
- App-based split tunneling: This approach splits tunnels by app instead of website URL. It’s perfect for excluding apps that are incompatible with VPNs. For example, some banking apps can block access if you log in from an unfamiliar location.
- Inverse split tunneling: By default, inverse split tunneling routes everything through the VPN except the apps and URLs you specify. If you don’t select an app to exclude from the encryption tunneling, then it will get encrypted.
How to Enable Split Tunneling for Your VPN Connection
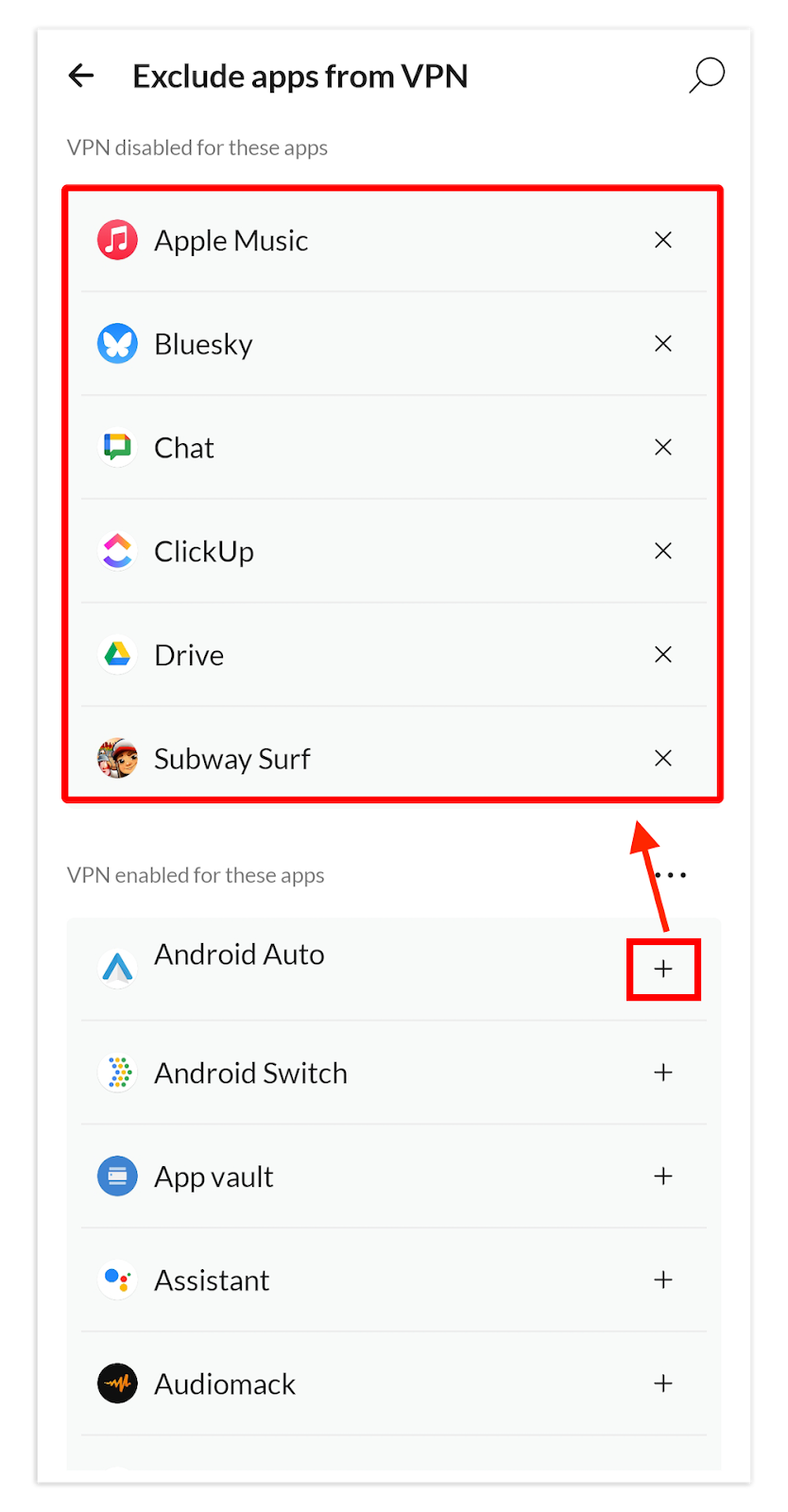
You can enable split tunneling for your VPN connection in the app settings, though the process varies with each VPN service. As an example, here’s how to enable it on NordVPN for Android, which uses app-based inverse split tunneling.
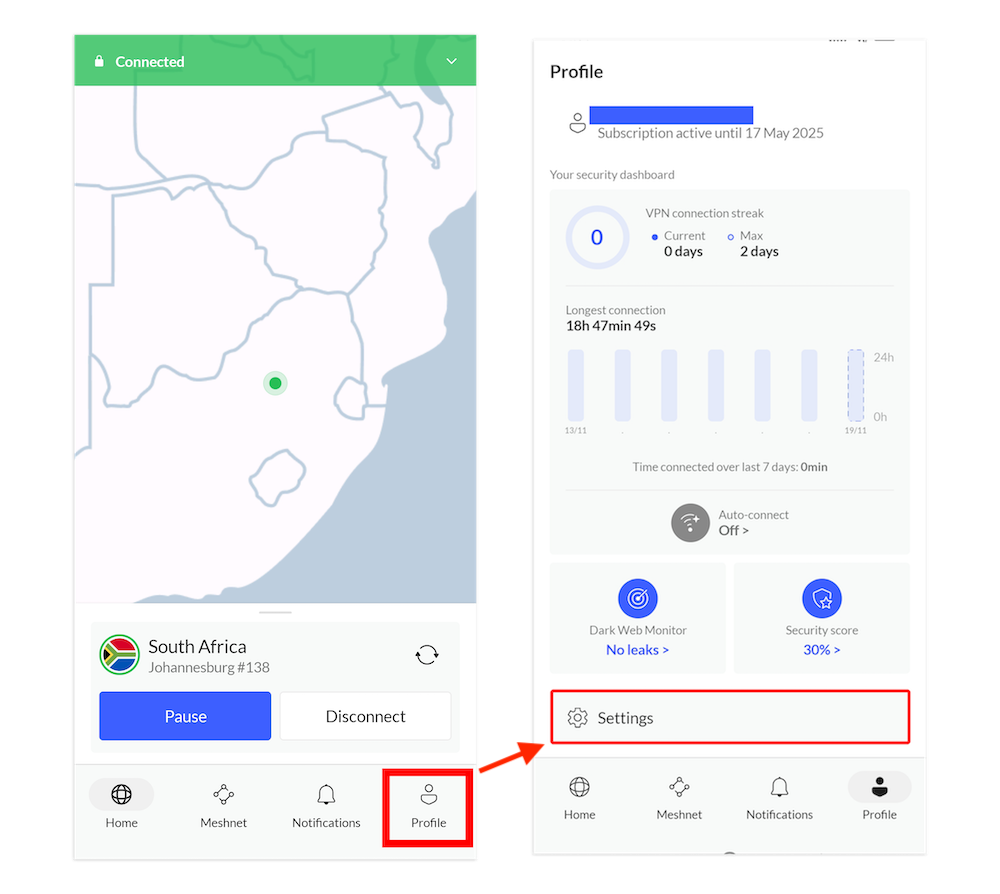
1. Open the Settings
Launch the VPN, select the “profile” icon at the bottom-right corner and tap the “settings” tab to access split tunneling.
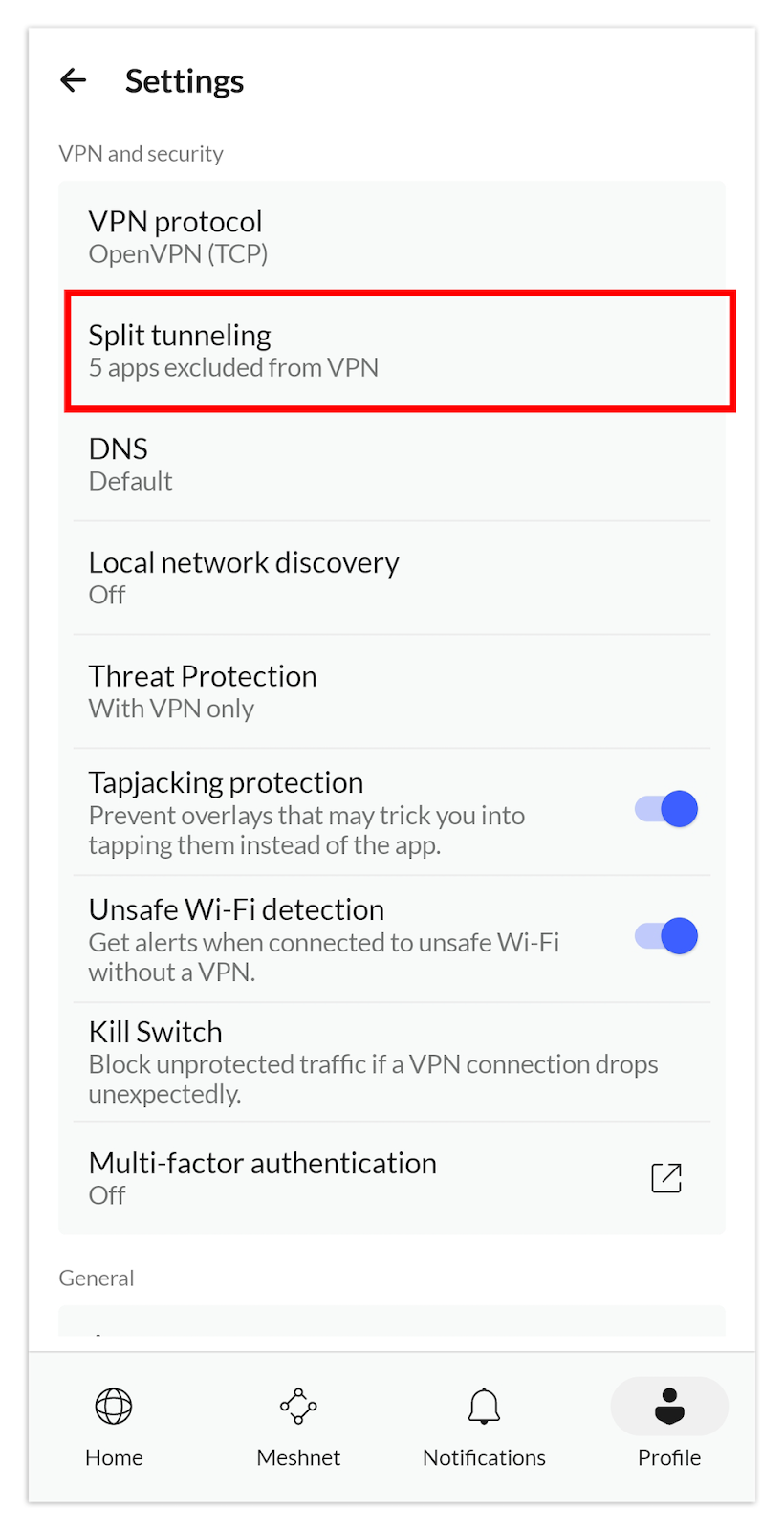
2. Open the Split Tunneling Tab
In the settings window, tap the “split tunneling” tab to open it.
3. Activate Split Tunneling
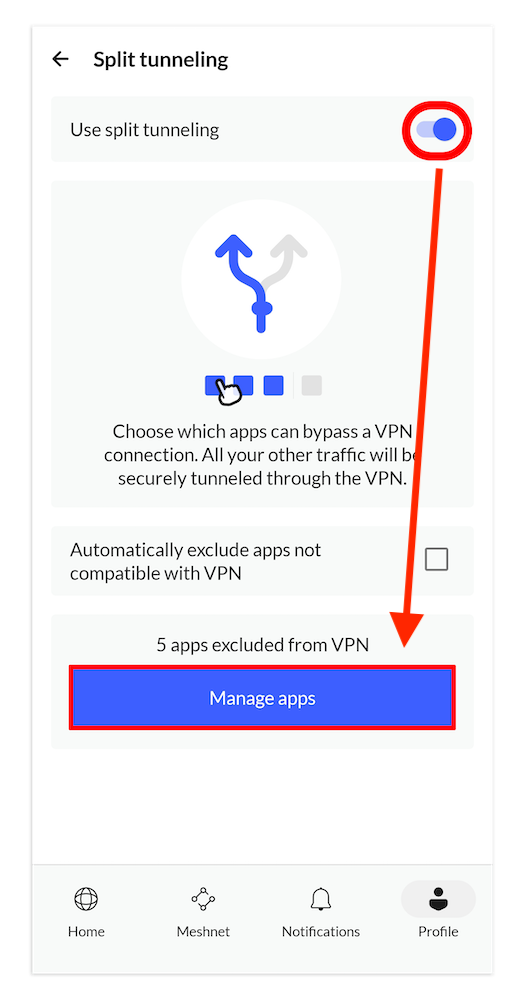
Toggle the “use split tunneling” button to activate it. Then, tap the “manage apps” button near the bottom to choose which apps can bypass the VPN connection.
4. Manage Your Apps
Under “manage apps,” scroll down the list and select the apps you want to exclude from the VPN connection by tapping the “+” sign next to each. To return an app back to the encrypted list, tap the “x” icon on the right. Split tunneling is now active.
Benefits & Drawbacks of a Split Tunnel VPN Connection
Using split tunneling has advantages and disadvantages.
Pros: Why Use the VPN Split Tunneling Feature
The following are some benefits of using a VPN’s split tunneling.
- Improved performance: Routing only selected apps or websites through the VPN reduces the average processing time of all your internet activities. This decreases the data load that must pass through your VPN tunnel, potentially improving speeds overall.
- Flexibility and control: Split tunneling allows you to manage multiple internet functions without losing vital security and speeds. For example, if you’re a remote worker, you can securely route important work traffic through the VPN while browsing casually with faster speeds through your regular connection.
- Easier remote connections: If you use a VPN to remotely access a corporate network, you can pass only work-related traffic through it. Split tunneling keeps your device running faster by not encrypting all your outgoing requests.
Cons: Why to Not Use VPN Split Tunnel Connection
Here are the drawbacks of using VPN split tunneling.
- Security vulnerabilities: If you mistakenly send important traffic outside the VPN tunnel, your activities and data may be exposed. This can be dangerous if you’re using unsecured public WiFi.
- Increased complexity: While split tunneling is easy to use on most VPNs, it requires complex configurations for remote work situations. It’s easy to misconfigure split tunneling or accidentally exclude sensitive data.
Is Split Tunneling Secure?
Split tunneling is secure because you are still using encryption, even when it focuses only on a portion of your traffic. No one can see anything within that encrypted data stream, including your browsing location and the sites you open.
However, you must know what you’re encrypting and what you’re leaving out. It’s easy to confuse the options to route through the VPN or bypass the VPN if you’re not paying attention.
For example, Surfshark’s split tunneling has both Route via VPN and Bypass VPN options. If you confuse these two, you could end up exposing traffic you intended to hide by setting sensitive traffic to bypass the VPN. It sounds simple, but it happens.
In light of that, I highly recommend encrypting everything to be on the safe side. Use split tunneling only if the impact of full tunneling on your internet speed is significant enough to make it unusable.
Split Tunneling Security Risk
A security risk associated with split tunneling is the potential exposure of unencrypted data to hackers, your ISP and other malicious parties. This threat goes up significantly when you use split tunneling on unsecured public hotspots. As long as part of your traffic is visible on public networks, you are at risk.
Misconfigurations could also mistakenly exclude a sensitive app or website from an encrypted VPN connection. This can be devastating in remote access environments where different networks and traffic are compartmentalized for security reasons.
The Best VPN With Split Tunneling
Some VPNs don’t have split tunneling. Those that do limit the feature to some operating systems. Here are the best split tunneling VPNs.
1. NordVPN Split Tunneling
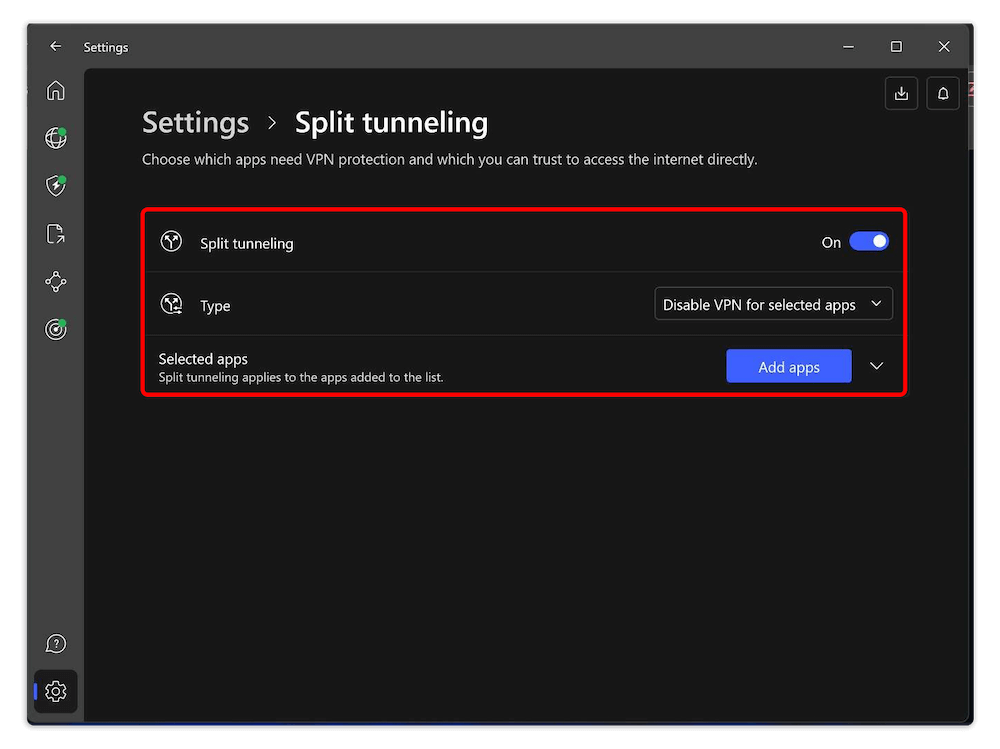
NordVPN offers app-based split tunneling on Android, Android TV and Windows (7, 8.1, 10 and 11) as well as URL-based split-tunneling on Chrome, Firefox and Edge. NordVPN for Android has an additional option to automatically exclude apps that aren’t compatible with VPNs.
This NordVPN review dives deeper into this feature and more. You can try NordVPN with a 30-day money-back guarantee.
2. Surfshark Split Tunneling
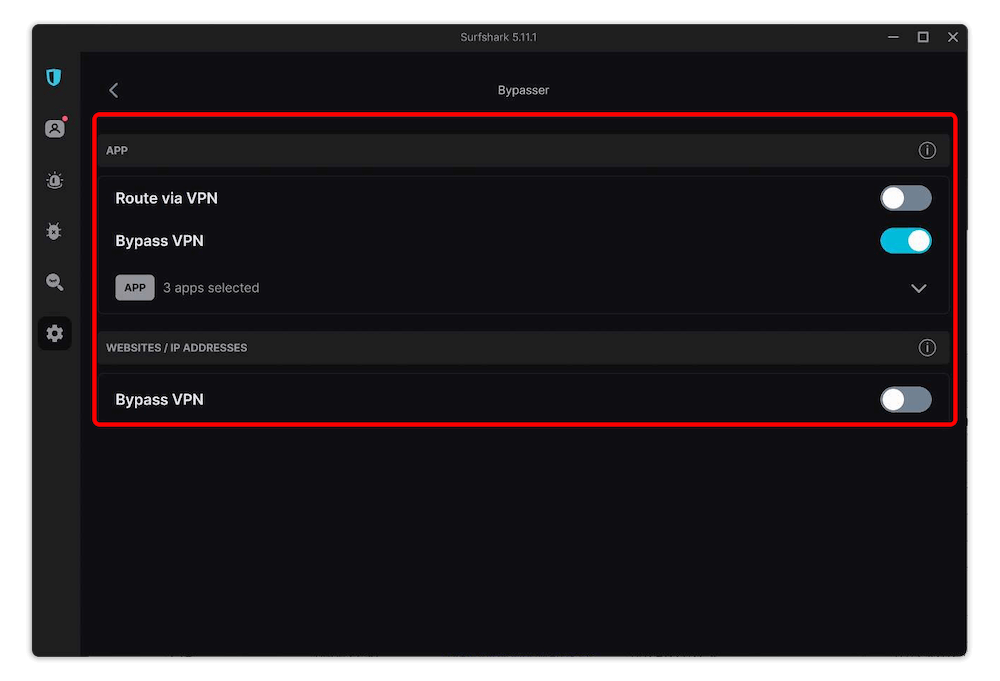
On Surfshark, split tunneling is called Bypasser and is available on Windows, Android and iOS. There are two Bypasser options. Route via VPN allows you to select which apps to encrypt, while Bypass VPN is an inverse split tunneling feature that encrypts everything that isn’t on the list.
Surfshark’s split tunneling for Android and iOS is both app-based and URL-based. On Windows, Route via VPN and Bypass VPN are app-based, and a separate Bypass VPN option exists for websites and IP addresses only. There’s also a URL-based Bypasser on Surfshark for Chrome, Firefox and Edge.
Find out more in this Surfshark review. You can also try Surfshark with a 30-day money-back guarantee on all plans.
3. ExpressVPN Split Tunneling
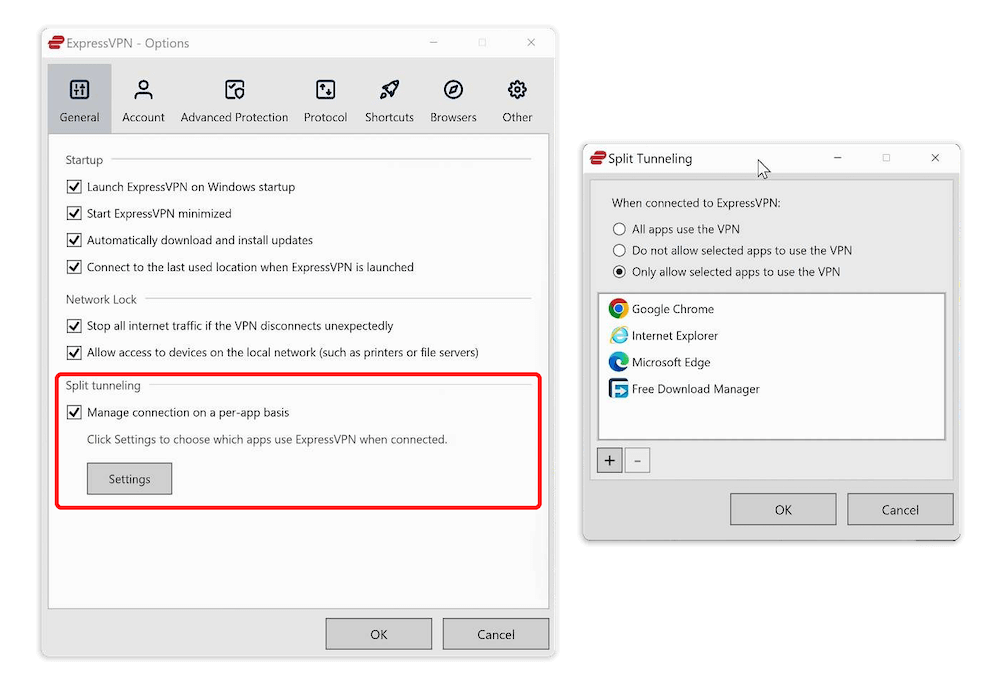
ExpressVPN offers app-based split tunneling on Android, Windows (10 and 11), macOS (pre-macOS Big Sur) and routers. None of ExpressVPN’s browser extensions allow split tunneling. This ExpressVPN review discusses all that and more. You can also try ExpressVPN with its 30-day money-back guarantee.
4. PIA Split Tunneling
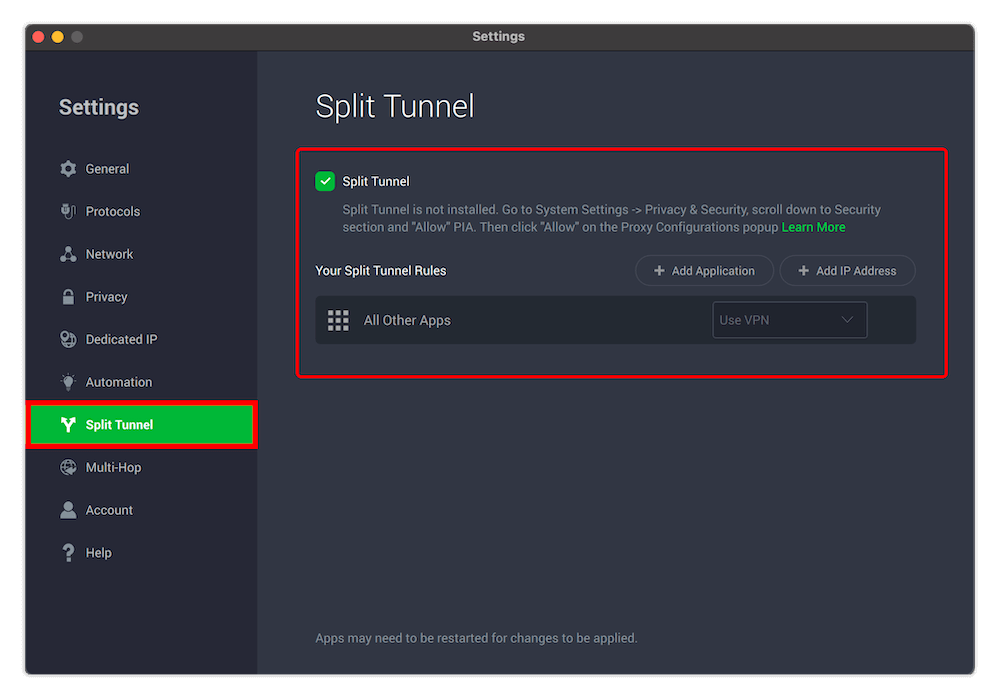
Private Internet Access has app-based and URL-based split tunneling on Android, Windows, Linux and macOS. You also get URL-based split tunneling called Bypass List on PIA’s browser extensions for Opera, Chrome and Firefox. On Android, split tunneling is known as Per App Settings; you can read more on that in this PIA review.
5. Proton VPN Split Tunneling
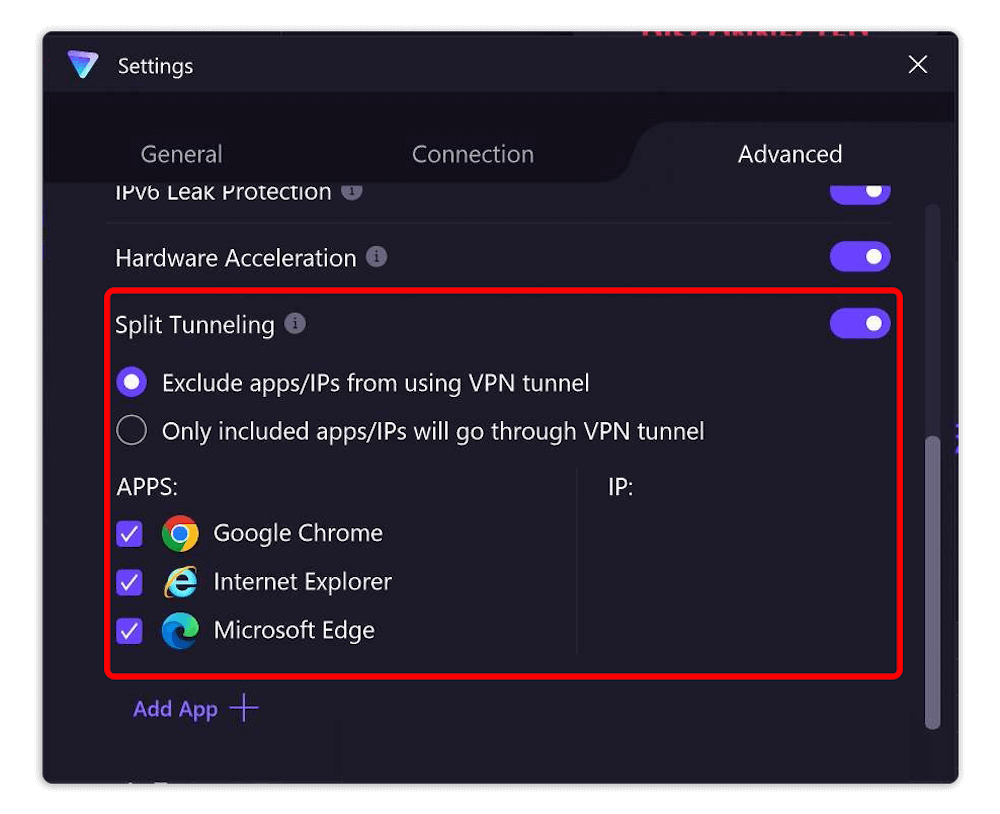
Proton supports app-based and URL-based split tunneling on Windows and Android, as well as app-based split tunneling on Android TV. You can also use URL-based split tunneling on all Proton VPN browser extensions.
There are two options: You can either exclude selected apps and IPs from using the regular VPN tunnel, or set some to be routed through the inverse VPN tunnel. Read this Proton VPN review for more details.
Conclusion: VPN Split Tunneling
Split tunneling offers the flexibility and control necessary to get the best out of your VPN connection. It can potentially improve your overall speeds as less traffic is being encrypted, although the difference may not be that significant. More important is your own freedom to set the parameters for how your VPN works.
However, exposing part of your traffic to third parties is risky, especially on public hotspots. Therefore, you should use split tunneling only as a last resort. My recommendation is to always go with full tunneling whenever you can.
Have you used split tunneling before? Did you experience any improvements in overall performance while using it? Tell us what you think in the comments below, and thank you for always reading our blog.
FAQ: Split Tunneling VPN Services
Which VPN Tunnel Style Routes Only Certain Types of Traffic?
Split tunnel style routes only certain types of traffic through a VPN tunnel.What Does Split Tunneling Do?
Split tunneling allows you to choose which apps and websites to route through the VPN and which to access over a regular internet network.What Is a Split Network?
A split network refers to an internet connection in which some traffic is routed through a virtual private network while the rest passes through a regular internet network.

Leave a Reply